There are so many acronyms in the networking and security field that can drive you crazy.
The terms IPS, IDS, WAF etc might be known acronyms in the field of network security but many beginner professionals sometimes have difficulty to understand the concept behind these technologies, how they compare etc.
In this article I’ll do my best to compare and break down the differences between IPS, IDS, Firewalls and WAF as they are very popular solutions used in networks for cyber security protection.
Let’s first see the meaning of each acronym:
IPS = Intrusion Prevention System
IDS = Intrusion Detection System
WAF = Web Application Firewall
How they Fit in a Network
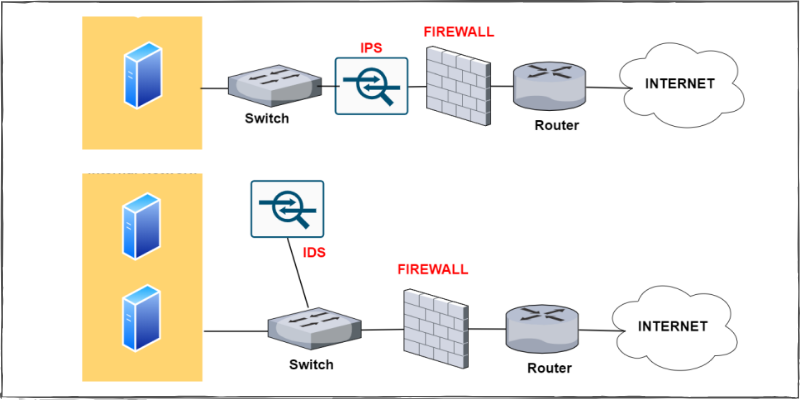
A picture is a thousand words. To get a quick idea of how these solutions/devices can be used in a network design, let’s see a topology below which includes all security solutions in a network (firewall, IPS, IDS, WAF).
The intention of the diagram below is to illustrate how these security devices are usually placed in networks.
Professionals should consider their own specific requirements and decide how to actually implement their own networks (for example, an IDS with an IPS in the same network might not be needed).
Let’s now briefly describe each security device and then compare them further below in this article.
Firewall
There are several types of firewalls but the most common one is the hardware network firewall. As you can see from all network diagrams in this article, the network firewall is found in all network designs since it’s the cornerstone of network security.
The core function of a firewall is to allow or block traffic between source hosts/networks and destination hosts/networks.
Basic firewalls work at the Layer 3 and Layer 4 of the OSI model, i.e they can allow or block IP packets based on source/destination IP addresses and source/destination TCP/UDP ports.
Moreover, a network firewall is stateful. This means that the firewall keeps track of the states of connections that pass through it.
For example, if an internal host successfully accesses an Internet website through the firewall, the latter will keep the connection inside its connection table so that reply packets from the external webserver will be allowed to pass to the internal host because they already belong to an established connection.
Nowadays, Next Generation Firewalls work all the way up to Layer 7 of the OSI models which means they are able to inspect and control traffic at the application level.
IPS
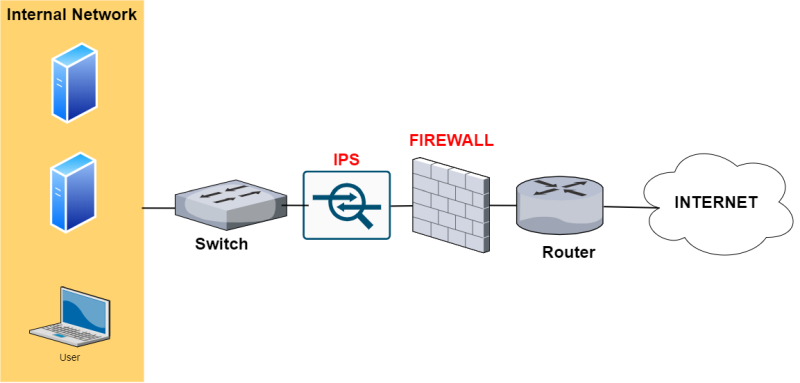
An Intrusion Prevention System (IPS), as the name suggests, is a security device with a main task of preventing network intrusions.
That’s why the IPS is connected in-line to the packet flow. As shown from the network topology above (Firewall with IPS), the IPS device is usually connected behind the firewall but in-line the communication path which transmits packets to/from the internal network.
The above placement is required in order for the IPS device to block malicious traffic immediately before reaching internal servers.
Usually an IPS is signature-based which means that it has a database of known malicious traffic, attacks and exploits and if it sees packets matching a signature then it blocks the traffic flow.
Also, an IPS can work with statistical anomaly detection, rules set by the administrator etc.
IDS
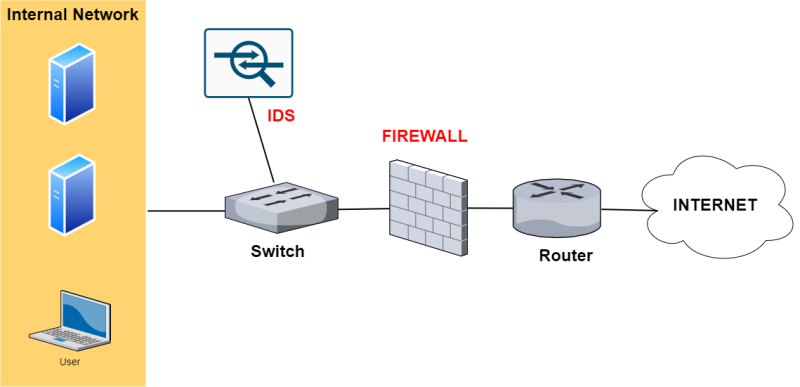
An IDS (Intrusion Detection System) is the predecessor of IPS and is passive in nature. As shown from the network above (Firewall with IDS), this device is not inserted in-line with the traffic but rather it is in parallel (placed out-of-band).
Traffic passing through the switch is also sent at the same time to the IDS for inspection. If a security anomaly is detected in the network traffic, the IDS will just raise an alarm (to the administrator) but it will not be able to block the traffic.
Similarly to IPS, the IDS device also uses mostly signatures of known security attacks and exploits in order to detect an intrusion attempt.
In order to send traffic to the IDS, the switch device must have a SPAN port configured in order to copy traffic and send it towards the IDS node.
Although an IDS is passive in the network (i.e it can’t actively block traffic), there are some models that can co-operate with the firewall in order to block a security attack.
For example, an IDS can send a command to the firewall in order to block specific packets if the IDS detects an attack.
WAF
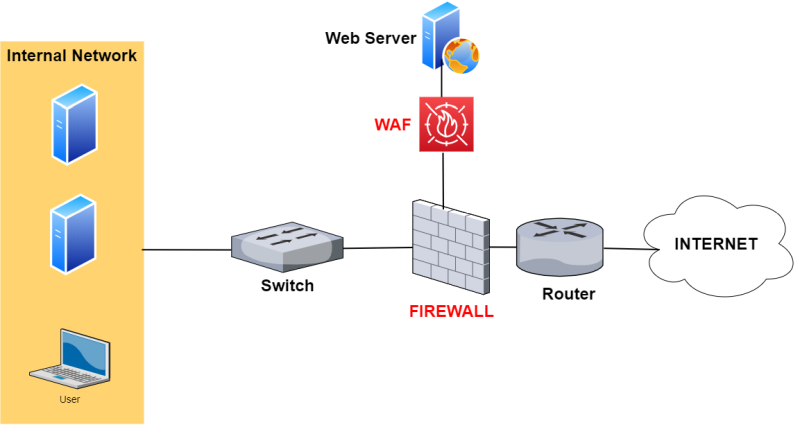
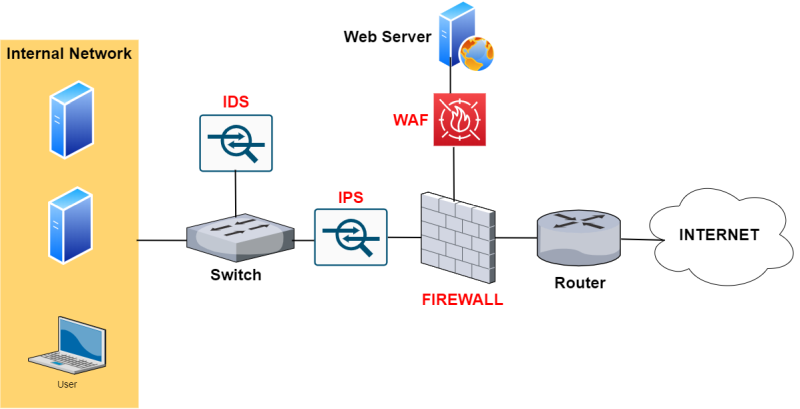
A WAF (Web Application Firewall) is focused on protecting websites (or web applications in general).
It works at the application Layer to inspect HTTP web traffic in order to detect malicious attacks targeted towards websites.
For example, a WAF will detect SQL Injection attacks, Cross Site Scripting, Javascript attacks, RFI/LFI attacks etc.
Since most websites nowadays use SSL (HTTPs), the WAF is able also to provide SSL acceleration and also SSL inspection by terminating the SSL session and inspect the traffic inside the connection on the WAF itself.
As shown from the network above (Firewall with WAF), it is placed in front of a Website (usually) in a DMZ zone of a firewall.
With a WAF in place, an administrator has the flexibility to restrict web access to specific parts of a website, to provide strong authentication, to inspect or limit file uploads to the website etc.
Let’s now see some quick comparison tables for the above security solutions.
IPS vs IDS
| IPS | IDS | |
| Network placement | In-line (in-series) with network traffic | Parallel (out-of-band) with traffic |
| Mode of operation | Active device. Can actively block attacking traffic. | Passive device. Cannot block attacking traffic, only detect. |
| Detection mechanisms | Signature-based, rule-based, statistical anomaly detection etc | Signature-based, rule-based, statistical anomaly detection etc |
| Blocking options | Block packets at network level, reset connection, alert the administrator etc | Alert the administrator, sends a reset connection request. |
| Hardware features | Must be high performance to perform Deep Packet Inspection and not slow down the traffic. | Does not need to be very high performance since it does not intervene in the traffic. However, in order to keep-up with traffic in real-time it must be able to handle the line bandwidth. |
Firewall vs IPS/IDS
| Firewall | IPS/IDS | |
| Network placement | Usually placed at the front of the network to control traffic. | Behind the firewall either as in-line or out-of-band. |
| Main use case | Allows or blocks traffic between different network zones. | Dedicated to inspect network packets to match them against signatures of known malicious attacks. Then, traffic is either blocked or an alarm is issued. |
| Detection mechanisms | Usually works up to Layer 4 to allow or block IP address and ports. | Signature-based, rule-based, statistical anomaly detection etc |
| Blocking options | Block or allow packets at the network level. | Detect attacks and either block traffic directly or send an alarm. |
| Hardware features | Usually have many physical network interfaces in order to segment the network into different security zones. | Must be high performance to perform Deep Packet Inspection and not slow down the traffic. |
WAF vs IPS/IDS
| WAF | IPS/IDS | |
| Network placement | Placed at the front of websites / web application | Behind the firewall either as in-line or out-of-band. |
| Main use case | Dedicated to inspect only HTTP web traffic and protect against web specific attacks. | Dedicated to inspect all network packets to match them against signatures of known malicious attacks. Then, traffic is either blocked or an alarm is issued. |
| Protecting against these Security Attacks (examples) | SQL injection, Cross Site Scripting, GET/POST attacks, session manipulation attacks, javascript, LFI/RFI etc | Exploits against services such as webservers, SMTP, RDP, DNS, windows OS, Linux OS etc. |
Related Posts
- 5 Best Practices to Keep Rogue Devices at Bay
- Cisco Talos Year in Review – Top Cyber Security Threats in 2023 and Beyond
- How to Scan an IP Network Range with NMAP (and Zenmap)
- What is Cisco Identity Services Engine (ISE)? Use Cases, How it is Used etc
- What is Cisco Umbrella Security Service? Discussion – Use Cases – Features