At its core, Cisco Identity Services Engine (ISE) is a type of Network Access Control Solution that uses policy-based decision making to determine if a device is allowed access to the network and, if allowed, what level of access this device is given.

Cisco ISE is a complex and feature packed Security Application that controls access to the network for both Wired and Wireless devices by employing mainly the 802.1x protocol and EAPoL (EAP over LAN).
ISE also provides Authentication, Authorization and Accounting (AAA) through the RADIUS protocol and Device Administration can be controlled through ISE by using the TACACS+ Service.
How ISE Authenticates Users and Devices
802.1x
The 802.1X protocol is commonly known as Dot1x and uses EAP (Extensible Authentication Protocol) and the RADIUS protocol together to provide Authentication for devices at the access level of the network.
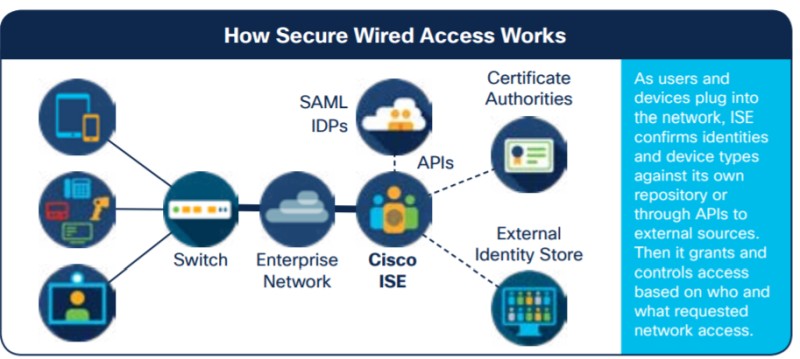
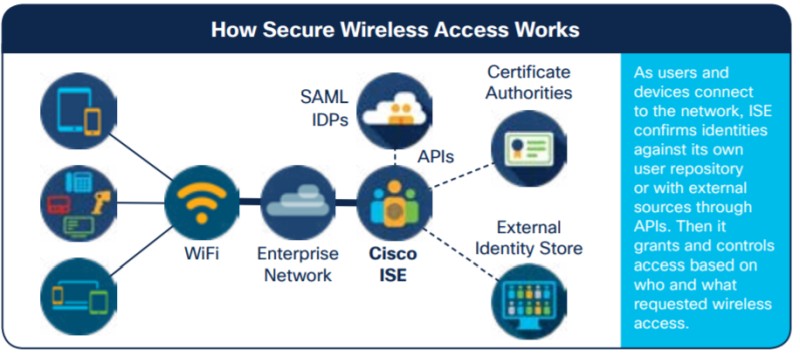
This access level of the network is usually the physical network switch interface or Wireless Access Point where the device is connecting to the network.
The Dot1x process consists of three components which are the Supplicant, the Authenticator, and the Authentication server.
- The Supplicant is a piece of software which allows the device to communicate using the EAP protocol.
- The Authenticator is the Network Infrastructure device, such as a Cisco Switch or Cisco Wireless LAN controller which acts as a middleman between the Supplicant and the Authentication Server.
- The Authentication Server is the AAA Server (working with the RADIUS protocol) which is a part of ISE.
The Supplicant and Authenticator communicate using an EAP protocol such as PEAP, EAP-TLS or EAP-FAST and then the Authenticator communicates with the Authentication Server using RADIUS.
The Supplicant never directly talks with the Authentication Server.
MAB
MAC Authentication Bypass (MAB) can be used to authenticate devices which are unable to use the EAP protocol.
Many legacy devices do not have a built in Supplicant and cannot authenticate using EAP, so a method is used to pass the MAC address of the connecting device to ISE.
Authorized MAC Addresses are stored within ISE in Identity Stores and the received MAC address is compared to the MAC addresses that are located within these Identity Stores.
If a match is found, then the device is authenticated if not the authentication fails.
As MAC addresses can be spoofed, MAB is not as secure as EAP which uses Public Key Infrastructure (PKI) certificates to prove the devices’ identity.
Microsoft Active Directory
Cisco ISE is also often used in conjunction with Microsoft Active Directory for confirming User identity.
For a small number of Users, it is possible to manually create individual entries within ISE’s Internal User Identity Store and this can be used to check the credentials of Users logging into the network.
For larger organisations with many Users this can be impractical and so Lightweight Directory Access Protocol (LDAP) is used to allow ISE to communicate with an existing Active Directory Infrastructure and interrogate the User credentials stored within this system.
For some organisations recently, their Active Directory infrastructure has been migrated to the Microsoft Azure Cloud and this AD infrastructure is only supported in ISE versions 3.0 and above.
Web Authentication for Guests
For Guests and Visitor devices it is often not possible or impractical to manually add these devices or Users to an Identity Store or add entries within Active Directory.
To authenticate Guests, these users are re-directed to a captive web portal where they can supply user credentials or a passcode to gain Guest access to the network.
Web authentication can take place on the Cisco WLC which is known as Local Web Authentication or through a portal hosted by ISE which is known as Central Web Authentication.
EasyConnect
This is a feature that was added to ISE in version 2.1 and allows a device which does not have a supplicant to authenticate to ISE through LDAP to Active Directory.
This feature restricts the Switchport to allow just enough communication to pass through for LDAP to work.
How is ISE used?
ISE has a lot of features and which of these features and services are used depend largely on the type of network and business use cases or the licence level that has been purchased.
Let’s briefly discuss a few popular use cases of ISE.
TACACS+ and Device Administration
ISE can be used to control administrative access to Network Infrastructure devices such as Routers and Switches.
By Using TACACS+ the type of commands that are allowed to run on these devices can be set and restricted for different Network Administrators where required.
When a user logs in and makes changes to the system, TACACS+ creates accounting logs of who logged in, at what time and what changes were made by that user while logged in.
Bring Your Own Device (BYOD)
In modern times it is normal for employees to bring their own devices to work and attach devices such as phones, tablets etc to the corporate network. Often these devices are used to access the same resources as a company issued device.
Cisco ISE allows employees to register their own devices on the network and use the dot1x, EAP-TLS or PEAP protocols to encrypt and protect their connection to the network in the same way as a corporate device.
ISE allows the number of devices that an employee can register to be restricted and by using the mydevices portal within ISE an employee can mark their device as lost or stolen or add and remove devices without the help of IT staff.
Should a device be reported as stolen, ISE will blacklist this device and prevent it from being used on the network.
Mobile Device Management (MDM)
Cisco ISE can integrate with different vendors of MDM software which allows the enrolment of PKI certificates and additional controls, such as remote wiping of corporate mobile devices.
An example of a compatible MDM would be Airwatch.
Device Posture Assessment
ISE can be used to enforce company policy for devices that are joined to the corporate network.
With an Apex license, ISE can carry out an assessment of a devices security posture and can check if the device meets certain security criteria before being allowed onto the network.
For example, a device can be checked to make sure it has an up-to-date Operating System software or that it has antivirus installed and up to date and ensure the device has not been rooted.
If a device fails this check, it can be placed into a quarantine Vlan until it becomes compliant and remediation instructions can be sent to the device.
Guest and Visitor Management
ISE can redirect Guests’ and Visitors’ web browsing sessions to different types of captive portals which are all managed and hosted from the ISE Server depending on what is required.
There are three different types of portals that can be configured for Guest and Visitor Access.
- Hotspot Portal – When a device connects to the Guest network or Guest SSID the browser on the device is redirected to the Hotspot Portal that is hosted by ISE. The Guest is then required to agree to an Acceptable Use Policy and enter a code to gain access to the internet. This type of portal is similar to what is used in a coffee shop or airport and does not require the Guest to provide any personal information.
- Sponsored Guest Portal – The credentials to gain access through this type of portal is created in advance by a Sponsor who is usually someone who works for the company. Once the guest is registered by the sponsor the credentials can be sent by ISE to an email or SMS that has been provided by the Guest. This type of portal is often used to allow contractors limited access to the company network and authorisation is required from the company who sets the account up in advance.
- Self-Registered Guest Portal – This type of portal allows guests to register themselves using an email address and other personal information without requiring authorization from a Sponsor or company employee.
Some Advantages of Cisco ISE
Visibility
All devices and their users are easily visible or searchable in the monitor section of ISE.
A lot of information such as where they are connected to the network and which policies are being enforced can be seen from the Live Log view within ISE.
It is easy to troubleshoot and identify devices which are struggling to authenticate or see which devices are not compliant with corporate policy and have been denied access.
Reduce the number of required SSID’s
When many Wireless SSID’s are in use to separate devices into different Vlans or departments this can have a detrimental effect on the performance of the wireless network.
More SSIDs mean more beacons which in turn equals less airtime for devices to transmit over the wireless medium.
By using Cisco ISE, a single SSID can be used for connecting all devices to the network and separate these devices into different VLANs, based on the type of device or type of user.
Policies that are configured within ISE determine which Vlans devices or users are placed into and these Vlans can be dynamically changed on the Wireless Lan Controller (WLC) or on the switch interface as required.
As an example, a HP Printer can be dynamically identified by ISE as a printer and then placed into the correct Vlan which all other HP printers are assigned to by matching a Policy that has been created to match HP Printers.
Android phones could be placed into a different Vlan than Apple phones just by creating a policy which says if the device is identified as an Apple Iphone, then assign this to Vlan 20, If the device is identified as an Android then assign this to Vlan 30.
Dynamically update Access Lists
DACLs or Dynamic Access Control Lists are pushed out to the switches and applied to the correct interfaces automatically based on which policy and authorization profiles are matched to a particular device.
Access lists can be managed in one central location rather than on the individual switch.
Easily remove unauthorized devices
Should a device be identified as anomalous or reported stolen, authorization for access to the network can be revoked with a single click.
Users can self-manage and report their devices as stolen through the mydevices portal which automatically blacklists the device and revokes network access for that device.
Portal Customization
Guest portals can be customized with corporate branding or logos through the use of 3rd party websites or by manually applying Jquery coding and CSS markup to the portal customization page.
TrustSec Model
This used to be known as Security Group Access and is a security model which identifies assets through the application of Security Group Tags (SGT).
These tags are applied at the device when it joins the network and is used to identify which group this device traffic belongs to throughout all points in the network.
SGTs can be used to separate devices into departments such as sales or finance and then rules can be applied to these tags in ISE to enforce security.
Deployment Models
The Cisco ISE architecture consists of different responsibilities or personas which are assigned to different systems.
There are 4 personas in total and these systems can be deployed in various ways.
- A single ISE node (server) can run all 4 personas but in large deployments these personas are usually distributed out to different ISE servers which run one persona on each machine.
- A two-node deployment offers redundancy. In this architecture there is an active ISE node and a standby ISE node. All transactions are replicated between the two nodes so that the secondary ISE note can be promoted to Active and take over should a failure occur. It should be noted that this transition from Standby to Active is not an automatic process in a two-node deployment and manual configuration is required to fail over a secondary ISE node to Primary.
- For large organisations a distributed deployment is often used. In this type of deployment each persona is run on its own individual ISE node. Failover and redundancy is automatic on a distributed ISE deployment.
The four different personas are as follows:
- Administration – This is the server where the administrator can configure ISE and make administrative changes to the security policy.
- Monitoring (MnT) – This Node acts as the centralized server for the monitoring services and logging services for creation of reports. Troubleshooting of the ISE deployment or connected devices is also carried out from this ISE Server.
- Policy Service Node (PSN) – This server is the main work horse of the ISE deployment and is responsible for enforcing the policies and handling all the RADIUS authentication requests. There can be multiple servers distributed throughout a network which run the PSN persona. The PSN is also responsible for hosting all the various web portals.
- pxGrid Node (PXG) – can be used to exchange policy and configuration data between nodes like sharing tags and policy objects between Cisco ISE and third party vendors.
The full ISE deployment made up of the different personas is referred to as an ‘ICE CUBE’.
ISE Licensing
Cisco ISE can use Traditional licensing methods where each licence is applied to the ISE node manually by using a PAK code or ISE can use smart licensing and communicate directly with a licensing server at Cisco to retrieve its licenses.
License usage is per endpoint that is registered with ISE. There are different license levels and consumption of the various licenses depends on what ISE features the endpoints are interacting with.
Valid license options include:
- ISE Base only – Every connected device consumes a base license and this covers Basic network access, AAA, Guest Management, MACsec and TrustSec.
- ISE Base and Plus – Required for BYOD, MSE integration for location services, profiling and feed services, Cisco PXGrid.
- ISE Base and Apex – Third party MDM integration, Posture Compliance
- ISE Base and Device Administration – Required for TACACS+
- ISE Base, Plus, Apex, and Device Administration – Full License covering every available feature.
Related Posts
- 5 Best Practices to Keep Rogue Devices at Bay
- Introduction to Cisco EEM (Embedded Event Manager)
- Cisco Talos Year in Review – Top Cyber Security Threats in 2023 and Beyond
- Monitoring Cisco Network Infrastructure: What to Look for in an Ideal Cisco Monitoring Tool
- How to Reset Cisco Router or Switch to Factory Settings