The firewall is the cornerstone of security in computer networks and I.T in general. In this website I have been talking extensively about the Cisco ASA firewall which is a classic example of a hardware network firewall.

However, there are some other types of firewalls used in large enterprises, SMB or even home networks. Some of these types of firewalls are very popular and some are rarely encountered by professionals (such as the type discussed at the end of this article).
The main reasons to implement a firewall device or firewall software in a network is to control traffic flow, allow or block traffic between hosts, restrict access to applications, inspect packets for malicious patterns etc.
The above can be accomplished in different Layers of the OSI model, starting from Layer 3 up to Layer 7 which is the application layer.
So, without further delay let’s see the various architectures and types of firewalls that you can find in your professional career.
1) Hardware Firewall
This is the most popular type of firewall. It is used extensively in modern networks either as border device (i.e to separate and protect the internal LAN network from the Internet or other non-trusted networks as shown below) or to segment and protect internal networks in large enterprises.

Hardware firewalls usually have many physical network interfaces which can be used to create different “security zones” which are essentially different Layer 3 subnets. Each physical interface can be further divided in “subinterfaces” which can further expand the protection zones.
Because the firewall is running on its own dedicated hardware appliance, it can handle large volumes of packets, thousands or millions of connections and generally they are high performance devices.
Some popular brands of hardware firewalls include Cisco ASA, Fortigate, Juniper, Checkpoint, Palo Alto, SonicWall etc.
2) Software Firewall
A classic example of a software firewall is the Windows Firewall installed by default on all Microsoft Windows operating systems. It is a host-based firewall and controls traffic and applications on end-user workstations or servers.
Some other examples of software host firewalls are those found on Linux machines such as IPTABLES, CSF etc.
However, software firewalls are not only host-based. There are several flavors of Open Source Software firewalls (such as pfSense, OPNSense, ClearOS etc) which can be installed on dedicated hardware (servers, Linux boxes etc) and thus create a dedicated hardware firewall device.
The first two types mentioned above are two broad categories of firewalls. Now let’s see some other types based on their architecture, how they handle traffic and on which Layer of the OSI model they work.
3) Stateful Inspection Firewalls
Almost all modern network firewalls incorporate the “stateful inspection” architecture. Let’s describe what that means exactly using the example communication below:
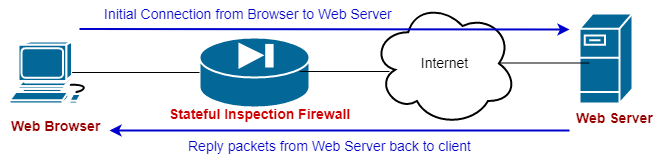
In a TCP communication between a client and a server (e.g a user with web browser communicating with a web server as shown above), the client browser starts an HTTP communication at port 80 with an Internet webserver.
Assume that the Stateful Inspection Firewall sitting in the middle allows this outgoing HTTP traffic to pass. Packets therefore will reach the Web Server which will reply back to the client (as happens with every TCP communication).
Now, the Stateful Firewall under the hood will save the details of the initiating connection from client to server in a “state table”. This table will include details such as source IP and source port, destination IP and destination port, TCP flags, TCP sequence numbers etc.
Therefore, any reply packets coming back from the external web server that match the initial connection started from the client, will pass through the firewall and reach the client without any extra configuration.
This makes the configuration easier since the administrator does not need to configure any rules on the firewall to allow the return/reply packets coming from outside to inside. These packets will be allowed automatically if they belong to an already established connection from client to server.
The stateful firewall is effective for three reasons.
- It works both on packets and on connections.
- It operates at a higher performance level than packet filtering or using a proxy server.
- It records data in a table for every connection and connectionless transaction. This table serves as a reference point for determining if packets belong to an existing connection or are from an unauthorized source.
4) Packet Filtering Firewall
A packet filtering firewall works at the Layer 3 and 4 of the OSI model (that is, Internet IP Layer and Transport Layer).
Having said that, this type of firewall filters traffic statically only by IP address and port numbers. There is no state kept by the firewall about each connection (like the stateful firewall we described above).
A packet filter device checks only the following:
- Source IP and port
- Destination IP and port
Packet filtering is also called “stateless firewall”. In Cisco devices for example an Access Control List (ACL) configured on a router works as a packet filter firewall.
One main disadvantage of packet filter firewalls is that you need to configure rules to allow also the reply packets that are coming back from destination hosts. This is because the firewall does not keep a “state table” like the stateful firewall we discussed above.
Packet Filtering is mostly implemented on Routers or Layer 3 switches and is a “quick and dirty” way to block some traffic from an untrusted network towards a trusted/protected network.
5) Application Firewall
As the name suggests, this type works at Layer 7 (application) of OSI model. It inspects and controls packets at the application level.
This firewall has knowledge of what constitutes safe or normal application traffic and what is malicious application traffic.
For example, an application firewall that protects a web server, knows about web related HTTP attacks (e.g SQL injections, Cross Site scripting etc) and protects the application from these attacks by looking into the HTTP application traffic.
Some examples of application firewalls include:
- WAF (Web Application Firewall): Protects websites/webservers
- DB (Database) Firewall: Protects Databases such as Oracle, MSSQL etc.
- Proxy Firewall: Inspects and protects traffic from users towards the internet. It can also provide URL/Domain web filtering. Users gain access to the network by going through a process that establishes session state, user authentication, and authorization policy.
6) Next-generation Firewall (NGFW)
This is mostly a marketing term which has been popular lately among firewall manufacturers. Basically, a NGFW combines almost all the types we have discussed above into one box. It is a stateful hardware firewall which also provides application level protection and inspection.
This type offers deep-packet inspection and is capable to identify malicious traffic in all Layers of the OSI model (up to the application layer).
A NGFW usually provides advanced intrusion detection/prevention, antivirus features, application control etc. These are usually licensed separately and the customer has to pay extra fees for enabling some/all of the protections.
Some NGFWs communicate with a cloud security service of the manufacturer (e.g Cisco Talos, Fortinet FortiGuard etc) in order to receive threat-intelligence info from the cloud.
7) Telephony Related Firewalls
There is a rare type of firewall which is not usually found in normal enterprise networks except in some specialized cases.
These are special firewalls related to telephony and VoIP services and are used to protect systems from telephony communication attacks.
Some examples include:
- SIP firewalls (to protect VoIP telephone systems).
- SMS firewalls (for GSM mobile networks to protect subscribers from SMS fraud attacks).
- SS7 firewalls (to protect mobile telephony operators).
What is Firewall Technology
Firewalls are used to protect computer networks from hostile intrusions. A hardware firewall separates trusted internal networks (e.g Internal corporate LAN) from external non-trusted networks (e.g Internet or untrusted WAN).
The primary objective of the firewall is to examine all inbound and outbound traffic to see if it meets specific criteria (firewall policy rules). If the traffic complies with the firewall policy it is permitted, otherwise it is dropped.
Related Posts
- 5 Best Practices to Keep Rogue Devices at Bay
- Cisco Talos Year in Review – Top Cyber Security Threats in 2023 and Beyond
- How to Scan an IP Network Range with NMAP (and Zenmap)
- What is Cisco Identity Services Engine (ISE)? Use Cases, How it is Used etc
- What is Cisco Umbrella Security Service? Discussion – Use Cases – Features