On my previous post I talked about Cisco ASA Active/Active configuration. In this post I will describe Active/Standby redundancy which is used much more frequently compared with the active/active scenario.
ASA Active/Standby failover/redundancy means connecting two identical ASA firewall units via LAN cable so that when one device or interface fails then the second one will take over the traffic and become the active device.
During normal operation, the active ASA will be synchronizing its configuration to the standby unit. The configuration must be changed on active ASA. If we try to change the configuration on standby ASA, then the following warning will be displayed:
ASA# configure terminal
**** WARNING ****
Configuration Replication is NOT performed from Standby unit to Active unit.
Configurations are no longer synchronized.
ASA(config)#
During active/standby failover, the active ASA receives all traffic flows and filters all network traffic while the secondary ASA is in the Ready mode. Therefore you should dimension each ASA device in such a way so that to be able to handle all traffic.
ASA failover works in 2 modes: Stateful Failover and Regular Failover. During regular Failover, when Failover occurs, all active connections will be dropped. During Stateful Failover however, the active unit continually passes per-connection state to standby unit.
When failover occurs, both ASA devices will have knowledge about all connections. The active ASA sends the state information of the following protocols/tables to the Standby ASA:
- NAT Translation Table
- TCP connection Table
- UDP Connection Table
- ARP Table
- Layer2 Bridge Table (if Transparent mode enabled)
- HTTP Connection Table (if HTTP Replication enabled)
- ISAKMP and SA Table
- GTP PDP Connection table
The following are not synchronized:
- HTTP connection Table (unless HTTP Replication Enable)
- Routing Table
- User Authentication (UAUTH) Table
- State Information for Security Service Module.
There are some predefined device requirements for allowing two ASAs to work in Failover mode: both of them must be the same model, both must have the same type and number of interfaces, the same volume of RAM and FLASH, the same licenses and the versions of ASA IOSs of both ASAs must match. If any of these requirements is not satisfied, then they cannot work in failover mode.
Let’s consider an example of active/standby Failover configuration (see diagram below). The Outside interfaces on ASAs are Ge0/0 and LAN interfaces are Ge0/1.
For Failover we will use Ge0/2, particularly Ge0/2.1 will be the Failover interface and Ge0/2.2 the state interface (by which the information about protocol States will be exchanged).
Note that you don’t have to use two different connections for Failover and State. They can share the same connection/interface.
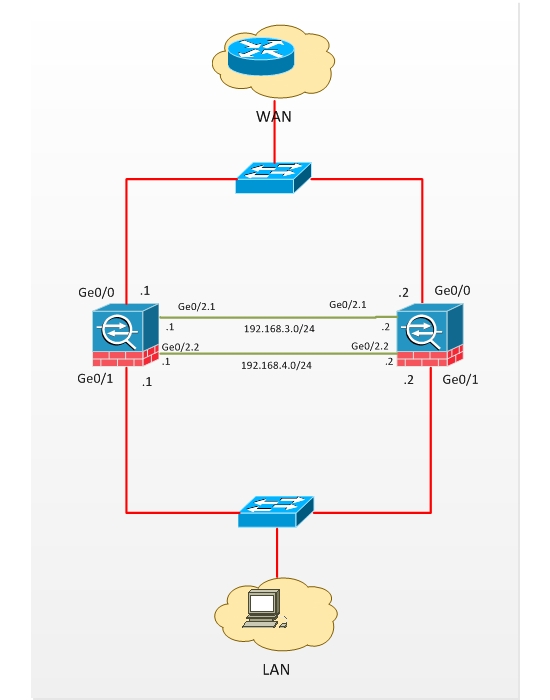
ASA Failover Configuration Example
Active Unit Configuration:
Note: Always start with the active ASA first.
!Assign IP address to outside interface. During Failover the primary IP address will be assigned to Standby Unit.
asa(config)# interface g0/0
asa(config-if)# ip address 192.168.1.1 255.255.255.0 standby 192.168.1.2
!Assign IP address to inside interface. During Failover the primary IP address will be assigned to Standby Unit.
asa(config)# interface g0/1
asa(config-if)# ip address 192.168.2.1 255.255.255.0 standby 192.168.2.2
!enable LAN Failover.
asa(config)#failover lan enable
!set that unit as primary.
asa(config)#failover lan unit primary
!Define Failover Interface. In this documentation, the “failover” (interface name for GigabitEthernet0/2.1) is used as a failover interface.
asa(config)#failover lan interface failover Ge0/2.1
!Assign IP address to Failover Interfaces.
asa(config)#failover interface ip failover 192.168.3.1 255.255.255.0 standby 192.168.3.2
In this documentation, the “state” (interface name for GigabitEthernet0/2.2) is used as a State
interface.
!Define stateful Failover interface
asa(config)#failover link state Ge0/2.2
!Assign IP addresses to Stateful Failover interfaces
asa(config)#failover interface ip state 192.168.4.1 255.255.255.0 standby 192.168.4.2
!enable Failover
asa(config)#failover
Note: Issue the failover command on the primary device first, and then issue it on the secondary device. After you issue the failover command on the secondary device, the secondary device immediately pulls the configuration from the primary device and sets itself as standby.
The primary ASA stays up and passes traffic normally and marks itself as the active device. From that point on, whenever a failure occurs on the active device, the standby device comes up as active.
Standby Unit Configuration:
! enable LAN Failover
asa(config)#failover lan enable
!Define the failover interface
asa(config)#failover lan interface failover Ge0/2.1
!assign IP address to failover interface
asa(config)#failover interface ip failover 192.168.3.1 255.255.255.0 standby 192.168.3.2
!set this unit as secondary
asa(config)#failover lan unit secondary
! Enable failover.
asa(config)#failover
After the above is completed, configuration replication will start with the following message:
“Beginning configuration replication: Sending to mate” ……….
“End Configuration Replication to mate.”
All configuration commands will be done on Primary unit from now on. Connect to the primary unit and issue the command “write memory” to save the configuration. Run also the command “write standby” to save the config to the secondary device.
Verification and Troubleshooting Commands:
!show failover on Primary ASA
asa # show failover
Failover On
Last Failover at: 05:12:14 tbilisi Dec 7 2010
This context: Active
Active time: 14228860 (sec)
Interface outside (192.168.1.1): Normal
Interface inside (192.168.2.1): Normal
Peer context: Standby Ready
Active time: 1104 (sec)
Interface outside (192.168.1.2): Normal
Interface inside (192.168.2.2): Normal
Stateful Failover Logical Update Statistics
Status: Configured.
Stateful Obj xmit xerr rcv rerr
RPC services 0 0 0 0
TCP conn 1217633001 31648 2774 0
UDP conn 1128592801 0 15204 0
ARP tbl 2435313 0 420 10
Xlate_Timeout 0 0 0 0
SIP Session 885790 0 0 0
! show failover on secondary unit.
asa# show failover
Failover On
Last Failover at: 05:12:14 tbilisi Dec 7 2010
This context: Standby Ready
Active time: 1104 (sec)
Interface outside (192.168.1.2): Normal
Interface inside (192.168.2.2): Normal
Peer context: Active
Active time: 14228965 (sec)
Interface outside (192.168.1.1): Normal
Interface inside (192.168.1.2 ): Normal
Stateful Failover Logical Update Statistics
Status: Configured.
Stateful Obj xmit xerr rcv rerr
RPC services 0 0 0 0
TCP conn 7349 638711328 571031340 112
UDP conn 45152 0 1136400282 886
ARP tbl 430 0 2435305 36
Xlate_Timeout 0 0 0 0
SIP Session 0 0 885779 11
Cisco ASA Redundant Interface Configuration
In addition to device-level failover as we’ve discussed above, you can also configure interface redundancy on the same chassis of a Cisco ASA firewall.
Basically you can create a logical interface pair bundle (called “interface redundant“) in which you include two physical interfaces.
If one of the interfaces fail, the second one in the redundancy pair takes over and starts passing traffic.
You can configure up to 8 redundant interface pairs. After you configure the redundant interface pair, all security appliance configuration refers to this logical redundant pair instead of the member physical interfaces.
The following guidelines should be followed for redundant interface and its members:
- You must first remove the name of the physical interface (using the no nameif command) before adding it to the logical redundant interface.
- Both member interfaces must be of the same physical type. That is they must be both GigabitEthernet or both Ethernet.
- The only configuration available to physical interfaces that are part of a redundant interface pair are physical parameters (i.e the shutdown command and the description command).
Redundant Interface Configuration Example:
ASA(config)# interface redundant 1
ASA(config-if)# member-interface gigabitethernet 0/0
ASA(config-if)# member-interface gigabitethernet 0/1
From now on, all interface related commands must refer to “interface redundant 1“.
So there you go. In this article we have discussed both Active/Standby failover configuration is Cisco ASA together with physical interface redundancy.
The Active/Standby setup on ASA has many use-cases and one very popular one is described here. You can place one ASA physical device in one building and the second one in a different building, thus providing also geographic redundancy.
The only requirement is that both ASA devices must be connected with a Layer 2 connection so that they can replicate the states and connections between each other.
Related Posts
- Prevent Spoofing Attacks on Cisco ASA using RPF
- Configuring Connection Limits on Cisco ASA Firewalls – Protect from DoS
- Configuring AAA Authentication-Authorization-Accounting on Cisco ASA Firewall (TACACS+, RADIUS)
- Cisco ASA Firewall Management Interface Configuration (with Example)
- How to Configure Access Control Lists on a Cisco ASA 5500/5500-X Firewall (with Examples)