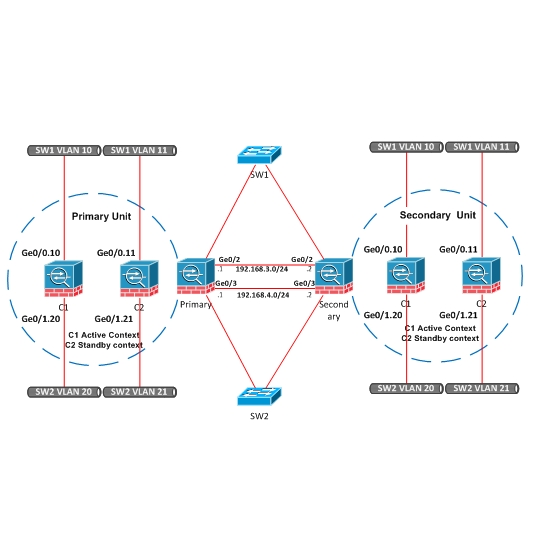
The Cisco ASA failover configuration requires two identical security appliances connected to each other through a dedicated failover link and, optionally, a stateful failover link.
The health of the active interfaces and units is monitored to determine if specific failover conditions are met. If those conditions are met, failover occurs.
In case of Active/Active configuration both Units carry traffic (unlike Active/Standby whereby only the active unit carries traffic). For creating active/active Failover, configuring both ASA devices in Multiple context mode is required.
For ASA redundancy scenario the two devices must be the same models, must have the same number and type of interfaces and the same license is required. ASA 5505 and 5510 do not support active/active failover without license upgrade.
For active/active configuration, Failover Contexts and Failover groups need to be created. The Failover group is then applied to Primary or Secondary physical ASA unit.
After this, the particular Failover group is applied to a Context. For example, primary unit is active ASA of Failover group1, but Secondary unit is Standby ASA of Failover group1. If primary ASA is out of order, Secondary ASA will become Active of Failover group1.
For explaining Active/Active Failover configuration in details, let’s do the following LAB.
Click on the image above for larger size diagram
Configuration Example
!Switch both ASA devices to multiple context mode.
asa(config)#mode multiple
!When ASAs are reloaded, connect them to each other with Ge0/2 and Ge0/3 ports. First start with the Primary Unit configuration. Before starting configuration, all interfaces must be in the up state.
!enable LAN Failover.
asa(config)#failover lan enable
!set this unit as primary.
asa(config)#failover lan unit primary
Determine Failover and State interfaces. These two interfaces can be the same physical interface if you don’t need to consume one extra port. In our example here we use two separate physical interfaces.
In this article, the “failover” (interface name for GigabitEthernet0/2) is used as a failover
interface.
!Define Failover Interface
asa(config)#failover lan interface failover Ge0/2
!assign IP address on Failover Interface. MUST be in same Subnet as the standby on the other unit.
asa(config)#failover interface ip failover 192.168.3.1 255.255.255.0 standby 192.168.3.2
In this documentation, the “state” (interface name for GigabitEthernet0/3) is used as a state
interface.
!Define stateful Failover interface
asa(config)#failover link state Ge0/3
!assign IP address on Stateful Failover interface
asa(config)#failover interface ip state 192.168.4.1 255.255.255.0 standby 192.168.4.2
!Create Failover groups, where Failover group1 will be the Primary, i.e. active on Primary Unit and Failover group2 will be the Standby on Primary Unit. Configure also HTTP Replication, after which occurs HTTP Connection state replication between active and Standby ASAs. Also determine Preempt Delay. Preempt Delay means in what time to regain role of Active after Fail Recovery.
asa(config)#failover group 1
asa(config-fover-group)#primary
asa(config-fover-group)#preempt 120
asa(config-fover-group)# replication http
asa(config)#failover group 2
asa(config-fover-group)#secondary
asa(config-fover-group)#preempt 120
asa(config-fover-group)# replication http
Now let’s start creating Contexts and assigning interfaces in each Context.
!Configure the admin context
asa(config)# admin-context admin
asa(config)# context admin
asa(config-ctx)# allocate-interface Management0/0
asa(config-ctx)# config-url disk0:/admin.cfg
!configure the Sub-interfaces
interface GigabitEthernet0/0.10
vlan 10
interface GigabitEthernet0/0.11
vlan 11
interface GigabitEthernet0/1.20
vlan 20
interface GigabitEthernet0/1.21
vlan 21
! Configure the contexts
asa(config)# context c1
asa(config-ctx)# allocate-interface gigabitethernet0/0.10
asa(config-ctx)# allocate-interface gigabitethernet0/1.20
asa(config-ctx)# config-url disk0:/c1.cfg
asa(config)# context c2
asa(config-ctx)# allocate-interface gigabitethernet0/0.11
asa(config-ctx)# allocate-interface gigabitethernet0/1.21
asa(config-ctx)# config-url disk0:/c2.cfg
!Snap each Context to Failover Groups. If we don’t indicate Contexts to Failover Groups, each context will be in Group1 by default.
asa(config)# context c1
asa(config-ctx)# join-failover-group 1
asa(config)# context c2
asa(config-ctx)# join-failover-group 2
!Configure IP addresses on Context1.
asa#changeto context c1
asa/c1# show running-config interface
!
interface GigabitEthernet0/0.10
nameif outside
security-level 0
ip address 192.168.10.1 255.255.255.0 standby 192.168.10.2
!
interface GigabitEthernet0/1.20
nameif inside
security-level 100
ip address 192.168.20.1 255.255.255.0 standby 192.168.20.2
!Configure IP addresses on Context2.
asa#changeto context c2
asa/c2# show running-config interface
!
interface GigabitEthernet0/0.11
nameif outside
security-level 0
ip address 192.168.11.1 255.255.255.0 standby 192.168.11.2
!
interface GigabitEthernet0/1.21
nameif inside
security-level 100
ip address 192.168.21.1 255.255.255.0 standby 192.168.21.2
!
Now let’s start Secondary Unit configuration.
!Define Failover Interface
asa(config)#failover lan interface failover Ge0/2
!assign IP address on Failover Interface. MUST be in same Subnet as other unit.
asa(config)#failover interface ip failover 192.168.3.1 255.255.255.0 standby 192.168.3.2
!enable LAN Failover.
asa(config)#failover lan enable
!set this unit as secondary
asa(config)#failover lan unit secondary
With the above piece of configuration commands everything is completed and now let’s start checking.
Verification and Troubleshooting Commands:
!verify Primary UNIT
asa# show failover
Failover On
Failover unit Primary
Failover LAN Interface: failover GigabitEthernet0/2 (up)
Unit Poll frequency 1 seconds, holdtime 15 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
Interface Policy 1
Monitored Interfaces 4 of 250 maximum
Version: Ours 8.2(1), Mate 8.2(1)
Group 1 last failover at: 05:12:14 tbilisi Dec 7 2010
Group 2 last failover at: 10:13:04 tbilisi Oct 24 2010
This host: Primary
Group 1 State: Active
Active time: 14536379 (sec)
Group 2 State: Standby Ready
Active time: 0 (sec)
slot 0: ASA5520 hw/sw rev (2.0/8.2(1)) status (Up Sys)
c1 Interface outside (192.168.10.1): Normal
c1 Interface inside (192.168.20.1): Normal
c2 Interface outside (192.168.11.1): Normal
c2 Interface inside (192.168.21.1): Normal
slot 1: empty
Other host: Secondary
Group 1 State: Standby Ready
Active time: 1104 (sec)
Group 2 State: Active
Active time: 14537266 (sec)
slot 0: ASA5520 hw/sw rev (2.0/8.2(1)) status (Up Sys)
c1 Interface outside (192.168.10.2): Normal
c1 Interface inside (192.168.20.2): Normal
c2 Interface outside (192.168.11.2): Normal
c2 Interface inside (192.168.22.2): Normal
slot 1: empty
Stateful Failover Logical Update Statistics
Link : state GigabitEthernet0/3.2 (up)
Stateful Obj xmit xerr rcv rerr
General 2405585244 0 75798262 188
sys cmd 1938317 0 1938317 0
up time 0 0 0 0
RPC services 0 0 0 0
TCP conn 1241561564 0 43443406 91
UDP conn 1157379296 0 28582971 84
ARP tbl 3799402 0 1833568 13
Xlate_Timeout 0 0 0 0
SIP Session 906665 0 0 0
Logical Update Queue Information
Cur Max Total
Recv Q: 0 49 90335543
Xmit Q: 0 7 2405585244
!verify Secondary unit
ASA# show failover
Failover On
Failover unit Secondary
Failover LAN Interface: failover GigabitEthernet0/2
Unit Poll frequency 1 seconds, holdtime 15 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
Interface Policy 1
Monitored Interfaces 4 of 250 maximum
Version: Ours 8.2(1), Mate 8.2(1)
Group 1 last failover at: 05:12:14 tbilisi Dec 7 2010
Group 2 last failover at: 10:13:03 tbilisi Oct 24 2010
This host: Secondary
Group 1 State: Standby Ready
Active time: 1104 (sec)
Group 2 State: Active
Active time: 14537372 (sec)
slot 0: ASA5540 hw/sw rev (2.0/8.2(1)) status (Up Sys)
c1 Interface outside (192.168.10.2): Normal
c1 Interface inside (192.168.20.2): Normal
c2 Interface outside (192.168.11.2): Normal
c2 Interface inside (192.168.21.2): Normal
slot 1: empty
Other host: Primary
Group 1 State: Active
Active time: 14536486 (sec)
Group 2 State: Standby Ready
Active time: 0 (sec)
slot 0: ASA5520 hw/sw rev (2.0/8.2(1)) status (Up Sys)
c1 Interface outside (192.168.10.1): Normal
c1 Interface inside (192.168.20.1): Normal
c2 Interface outside (192.168.11.1): Normal
c2 Interface inside (192.168.21.1): Normal
slot 1: empty
Stateful Failover Logical Update Statistics
Link : state GigabitEthernet0/3.2 (up)
Stateful Obj xmit xerr rcv rerr
General 111758344 0 1089580597 1046
sys cmd 1938331 0 1938331 0
up time 0 0 0 0
RPC services 0 0 0 0
TCP conn 73801356 0 581933209 113
UDP conn 34185062 0 501003000 886
ARP tbl 1833595 0 3799403 36
Xlate_Timeout 0 0 0 0
SIP Session 0 0 906654 11
Logical Update Queue Information
Cur Max Total
Recv Q: 0 7 1104118240
Xmit Q: 0 1 111758344
As we observed from above, active/active Failover is working and everything is as expected.
Related Posts
- Prevent Spoofing Attacks on Cisco ASA using RPF
- Configuring Connection Limits on Cisco ASA Firewalls – Protect from DoS
- Configuring AAA Authentication-Authorization-Accounting on Cisco ASA Firewall (TACACS+, RADIUS)
- Cisco ASA Firewall Management Interface Configuration (with Example)
- How to Configure Access Control Lists on a Cisco ASA 5500/5500-X Firewall (with Examples)