A common attack found on TCP/IP networks is IP spoofing. This is usually used for Denial-of-Service, Identity hiding, or even to bypass firewalls or Access-Lists security rules. The spoofing attack works like that:
- A malicious attacker sends packets towards a target host.
- The attacker disguises itself by inserting a fake source IP into the packet. This fake source IP address in the packet either does not exist at all or it might be a legitimate IP address of some other host located on some other network.
- The reply traffic from the target will never reach the attacker because the attacker’s source address is bogus. Therefore the identity of the attacker remains unknown.
- This can cause resource-exhaustion on the target host because it will create several “incomplete” TCP connections in its memory.
A Cisco ASA Firewall can identify a spoofed packet by using Reverse Path Forwarding (RPF or Unicast RPF – uRPF).
RPF can be enabled on a per interface basis. As soon as RPF is enabled on a specific interface, the ASA firewall will examine the source IP address (in addition to the destination address) of each packet arriving at this interface.
Normally, any Layer 3 network device examines only the destination address of packets in order to know how to route the packet.
By examining also the source IP address of the packet, the firewall can verify if the packet is spoofed or not.
The firewall will try to find the reverse route (the path back towards the source) in its routing table. If a reverse route is not found on the interface where the packet arrived, it means that the packet is spoofed and will be dropped immediately.
Lets see the diagram below to clarify the concept of Reverse Path Forwarding:
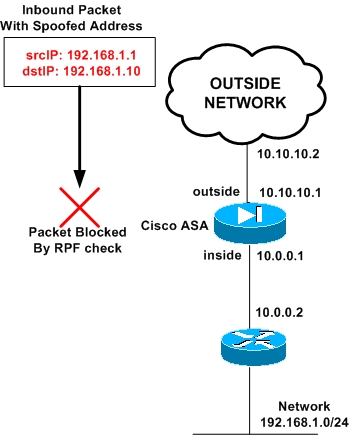
From the diagram above, an attacker tries to spoof the inside network 192.168.1.0 by using a fake source IP in the packet (fake source IP 192.168.1.1). It sends the packet towards its target host which is 192.168.1.10 (destination address in packet).
On the ASA we have configured RPF on the outside interface as following:
Ciscoasa(config)# ip verify reverse-path interface outside
The ASA will examine the source address of the spoofed inbound packet and will see that source IP 192.168.1.1 belongs to its internal network.
A packet with such a source IP should never arrive from the outside interface. Therefore the packet will be dropped.
The ASA performs the RPF check by using its routing table. The routing table shows that network 192.168.1.0/24 is towards the inside interface of ASA (assume that we have already configured a static route for this internal network).
Checking Statistics of uRPF Dropped Packets
If you want to check how many spoofed packets the ASA has dropped so far, you can run the following commands:
Ciscoasa# show ip verify statistics interface outside (stats just for the outside interface)
Ciscoasa# show ip verify statistics interface inside (stats just for the inside interface)
Ciscoasa# show ip verify statistics (stats for all interfaces)
Note:
RPF on Cisco ASA works on unicast traffic and checks packets of TCP, UDP and ICMP protocols.
Related Posts
- Configuring Connection Limits on Cisco ASA Firewalls – Protect from DoS
- Configuring AAA Authentication-Authorization-Accounting on Cisco ASA Firewall (TACACS+, RADIUS)
- Cisco ASA Firewall Management Interface Configuration (with Example)
- How to Configure Access Control Lists on a Cisco ASA 5500/5500-X Firewall (with Examples)
- Cisco ASA Firewall Packet Tracer for Network Troubleshooting