Cisco Adaptive Security Appliance (ASA) is quite a versatile device integrating application-aware firewall, SSL and IPsec VPN, intrusion prevention system (IPS), antivirus, antispam, antiphishing, and web filtering services. Cisco ASA also supports routing protocols such as Routing Information Protocol (RIP), Enhanced Interior Gateway Routing Protocol (EIGRP), and last but not least, Open Shortest Path First (OSPF). In this tutorial, our focus will be OSPF configuration on Cisco ASA according to the figure below.
Figure 1 OSPF on Cisco ASA
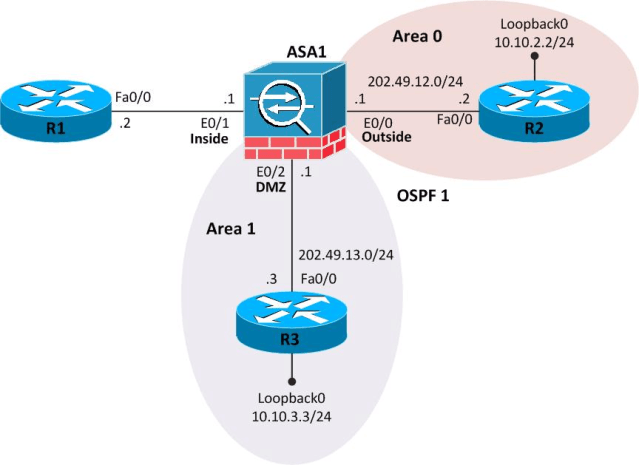
Please note that configuration on R1 is not relevant to this scenario and R1 is just shown for the sake of completeness.
Routers Config
We will start by configuring OSPF on routers R2 and R3. We would also configure MD5 authentication for OSPF on Fa0/0 of R2 and R3, using cisco as the authentication key.
Here’s the configuration for R2:
R2#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#interface FastEthernet0/0
R2(config-if)#ip address 202.49.12.2 255.255.255.0
R2(config-if)#ip ospf authentication message-digest
R2(config-if)#ip ospf message-digest-key 1 md5 cisco
R2(config-if)#exit
R2(config)#interface Loopback0
R2(config-if)#ip address 10.10.2.2 255.255.255.0
R2(config-if)#exit
R2(config)#router ospf 1
R2(config-router)#network 202.49.12.0 0.0.0.255 area 0
R2(config-router)#network 10.10.2.0 0.0.0.255 area 0
R2(config-router)#end
Here goes the configuration for R3:
R3#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#interface FastEthernet0/0
R3(config-if)#ip address 202.49.13.3 255.255.255.0
R3(config-if)#ip ospf authentication message-digest
R3(config-if)#ip ospf message-digest-key 1 md5 cisco
R3(config-if)#exit
R3(config)#interface Loopback0
R3(config-if)#ip address 10.10.3.3 255.255.255.0
R3(config-if)#exit
R3(config)#router ospf 1
R3(config-router)#network 202.49.13.0 0.0.0.255 area 1
R3(config-router)#network 10.10.3.0 0.0.0.255 area 1
R3(config-router)#end
Cisco ASA Configuration
Let’s now move to the interesting part where we will configure Cisco ASA. We will first configure interface IP addresses, at the same time assigning Ethernet0/0, Ethernet0/1, and Ethernet 0/2 to outside, inside, and DMZ (de-militarized zone) zones, respectively.
Inside and outside interfaces are assigned default security levels of 100 and 0 automatically. The higher the security level, the more secure an interface is. Therefore, the most secured network is placed behind an interface with a security level of 100, whereas the least secured network is placed behind an interface with a security level of 0.
A DMZ interface can be assigned a security level between 0 and 100. We assigned a security level of 50 to the DMZ interface using the security-level command.
We will also configure MD5 authentication for OSPF on the outside and DMZ interfaces choosing cisco as the authentication key.
Towards the end of configuration given below, both outside and DMZ interfaces are assigned to the appropriate OSPF area using the network command.
ASA1# configure terminal
ASA1(config)# interface Ethernet0/0
ASA1(config-if)# ip address 202.49.12.1 255.255.255.0
ASA1(config-if)# nameif outside
INFO: Security level for “outside” set to 0 by default.
ASA1(config-if)# ospf authentication message-digest
ASA1(config-if)# ospf message-digest-key 1 md5 cisco
ASA1(config-if)# exit
ASA1(config)# interface Ethernet0/1
ASA1(config-if)# ip address 192.168.1.1 255.255.255.0
ASA1(config-if)# nameif inside
INFO: Security level for “inside” set to 100 by default.
ASA1(config-if)# exit
ASA1(config)# interface Ethernet0/2
ASA1(config-if)# ip address 202.49.13.1 255.255.255.0
ASA1(config-if)# nameif DMZ
ASA1(config-if)# security-level 50
ASA1(config-if)# ospf authentication message-digest
ASA1(config-if)# ospf message-digest-key 1 md5 cisco
ASA1(config-if)# exit
ASA1(config)# router ospf 1
ASA1(config-router)# network 202.49.12.0 255.255.255.0 area 0
ASA1(config-router)# network 202.49.13.0 255.255.255.0 area 1
ASA1(config-router)#end
ASA1#
Troubleshooting and Verification Commands
Let’s now verify that ASA1 has indeed established OSPF adjacency with R2 and R3 using show ospf neighbor command.
ASA1# show ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
10.10.2.2 1 FULL/DR 0:00:32 202.49.12.2 outside
10.10.3.3 1 FULL/BDR 0:00:38 202.49.13.3 DMZ
The above output indicates that OSPF neighbor relationships have been successfully established with both R2 and R3. You can use show ospf interface command to find out more details such as OSPF neighbor authentication status.
ASA1# show ospf interface
outside is up, line protocol is up
Internet Address 202.49.12.1 mask 255.255.255.0, Area 0
Process ID 1, Router ID 202.49.13.1, Network Type BROADCAST, Cost: 10
Transmit Delay is 1 sec, State BDR, Priority 1
Designated Router (ID) 10.10.2.2, Interface address 202.49.12.2
Backup Designated router (ID) 202.49.13.1, Interface address 202.49.12.1
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
Hello due in 0:00:00
Index 1/1, flood queue length 0
Next 0x0(0)/0x0(0)
Last flood scan length is 2, maximum is 2
Last flood scan time is 0 msec, maximum is 0 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.10.2.2 (Designated Router)
Suppress hello for 0 neighbor(s)
Message digest authentication enabled
Youngest key id is 1
You can also use show ip ospf interface brief and show ip ospf neighbor commands on R2 and/or R3. We are showing the output of these two commands for R2 here.
R2#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
202.49.13.1 1 FULL/BDR 00:00:30 202.49.12.1 FastEthernet0/0
R2#show ip ospf interface brief
Interface PID Area IP Address/Mask Cost State Nbrs F/C
Lo0 1 0 10.10.2.2/24 1 LOOP 0/0
Fa0/0 1 0 202.49.12.2/24 1 DR 1/1
We can expect that R2, R3, and ASA1 may also have learned some OSPF routes by now. Let’s verify that by using show ip route command on R2 first.
R2#show ip route
<Some output omitted for brevity>
Gateway of last resort is not set
C 202.49.12.0/24 is directly connected, FastEthernet0/0
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
O IA 10.10.3.3/32 [110/12] via 202.49.12.1, 02:01:57, FastEthernet0/0
C 10.10.2.0/24 is directly connected, Loopback0
O IA 202.49.13.0/24 [110/11] via 202.49.12.1, 02:02:01, FastEthernet0/0
Please feel free at this point to use show ip route command on R3 as well. We can use show route command on ASA1 to find out which routes it has learned over OSPF.
ASA1# show route
<Some output omitted for brevity>
Gateway of last resort is not set
C 202.49.12.0 255.255.255.0 is directly connected, outside
O 10.10.3.3 255.255.255.255 [110/11] via 202.49.13.3, 2:03:52, DMZ
O 10.10.2.2 255.255.255.255 [110/11] via 202.49.12.2, 2:11:30, outside
C 202.49.13.0 255.255.255.0 is directly connected, DMZ
C 192.168.1.0 255.255.255.0 is directly connected, inside
Though OSPF routing is looking good at this stage, we may not yet be able to ping from R2 to R3 or vice versa.
On Cisco ASA, you do not need to define an ACL to permit traffic from a high security level interface to a low security level interface by default.
However, an ACL must explicitly permit traffic from a low security level interface (such as outside with security level 0) to a high security level interface (such as DMZ with security level 50).
Here is how we configure an ACL and apply it inbound to the outside interface to allow incoming traffic. Just for example purposes, we will allow icmp traffic from outside to IP 10.10.3.3 in DMZ.
access-list OUTSIDE-IN extended permit icmp any host 10.10.3.3
access-list OUTSIDE-IN extended permit icmp any any echo-reply
access-group OUTSIDE-IN in interface outside
Let’s try to ping from R2 to Loopback0 on R3 and vice versa, in order to seal the deal.
R2#ping 10.10.3.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.3.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/27/40 ms
R3#ping 10.10.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 12/24/44 ms
Related Posts
- Prevent Spoofing Attacks on Cisco ASA using RPF
- Configuring Connection Limits on Cisco ASA Firewalls – Protect from DoS
- Configuring AAA Authentication-Authorization-Accounting on Cisco ASA Firewall (TACACS+, RADIUS)
- Cisco ASA Firewall Management Interface Configuration (with Example)
- How to Configure Access Control Lists on a Cisco ASA 5500/5500-X Firewall (with Examples)