The Cisco ASA 5505 Firewall is the smallest model in the new 5500 Cisco series of hardware appliances. Although this model is suitable for small businesses, branch offices or even home use, its firewall security capabilities are the same as the biggest models (5510, 5520, 5540 etc).
The Adaptive Security technology of the ASA firewalls offers solid and reliable firewall protection, advanced application aware security, denial of service attack protection and much more.
Moreover, the performance of the ASA 5505 appliance supports 150Mbps firewall throughput and 4000 firewall connections per second, which is more than enough for small networks.
EDIT: There are newer models that will replace the ASA5505 as described here.
In this article I will explain the basic configuration steps needed to setup a Cisco 5505 ASA firewall for connecting a small network to the Internet.
We assume that our ISP has assigned us a static public IP address (e.g 200.200.200.1 as an example) and that our internal network range is 192.168.1.0/24.
We will use Port Address Translation (PAT) to translate our internal IP addresses to the public address of the outside interface.
The difference of the 5505 model from the bigger ASA models is that it has an 8-port 10/100 switch which acts as Layer 2 only.
That is, you can not configure the physical ports as Layer 3 ports, rather you have to create interface Vlans and assign the Layer 2 interfaces in each VLAN.
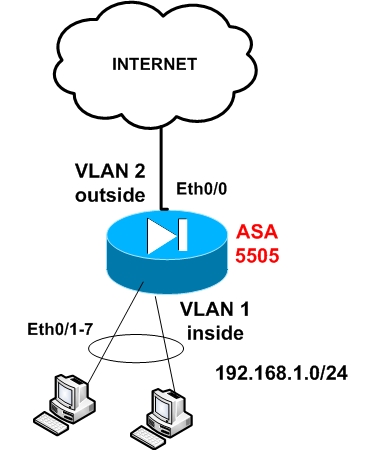
By default, interface Ethernet0/0 is assigned to VLAN 2 and its the outside interface (the one which connects to the Internet), and the other 7 interfaces (Ethernet0/1 to 0/7) are assigned by default to VLAN 1 and are used for connecting to the internal network.
Let’s see the basic configuration setup of the most important steps that you need to configure. The diagram below illustrates the network topology for the configuration setup that we will describe.
Notice from the diagram that port Ethernet0/0 connects to the Internet, and ports Ethernet0/1 to 7 connect to internal hosts (PC computers etc).
Step1: Configure the internal interface vlan
ASA5505(config)# interface Vlan 1
ASA5505(config-if)# nameif inside
ASA5505(config-if)# security-level 100
ASA5505(config-if)# ip address 192.168.1.1 255.255.255.0
ASA5505(config-if)# no shut
Step 2: Configure the external interface vlan (connected to Internet)
ASA5505(config)# interface Vlan 2
ASA5505(config-if)# nameif outside
ASA5505(config-if)# security-level 0
ASA5505(config-if)# ip address 200.200.200.1 255.255.255.0
ASA5505(config-if)# no shut
Step 3: Assign Ethernet 0/0 to Vlan 2
ASA5505(config)# interface Ethernet0/0
ASA5505(config-if)# switchport access vlan 2
ASA5505(config-if)# no shut
Step 4: Enable the rest interfaces with no shut
ASA5505(config)# interface Ethernet0/1
ASA5505(config-if)# no shut
Do the same for Ethernet0/1 to 0/7.
Step 5: Configure PAT on the outside interface
ASA5505(config)# global (outside) 1 interface
ASA5505(config)# nat (inside) 1 0.0.0.0 0.0.0.0
UPDATE for ASA Version 8.3 and later
From March 2010, Cisco announced the new Cisco ASA software version 8.3. This version introduced several important configuration changes, especially on the NAT/PAT mechanism. The “global” command is no longer supported. NAT (static and dynamic) and PAT are configured under network objects. The PAT configuration below is for ASA 8.3 and later:
object network obj_any
subnet 0.0.0.0 0.0.0.0
nat (inside,outside) dynamic interface
Step 6: Configure default route towards the ISP (assume default gateway is 200.200.200.2)
ASA5505(config)# route outside 0.0.0.0 0.0.0.0 200.200.200.2 1
The above steps are the absolutely necessary steps you need to configure for making the appliance operational. Of course there are much more configuration details that you need to implement in order to enhance the security and functionality of your appliance, such as Access Control Lists, Static NAT, DHCP, DMZ zones, authentication etc.
Download the best configuration tutorial for any Cisco ASA 5500 Firewall model HERE.
Here is also a new article I’ve written for a basic and advanced Configuration Tutorial for the new ASA 5506-X model.
DOWNLOAD THIS ARTICLE AS PDF FILE
Related Posts
- Prevent Spoofing Attacks on Cisco ASA using RPF
- Configuring Connection Limits on Cisco ASA Firewalls – Protect from DoS
- Configuring AAA Authentication-Authorization-Accounting on Cisco ASA Firewall (TACACS+, RADIUS)
- Cisco ASA Firewall Management Interface Configuration (with Example)
- How to Configure Access Control Lists on a Cisco ASA 5500/5500-X Firewall (with Examples)