Cisco devices offer excellent features for traffic filtering. The classic Access Control List (ACL) is the core mechanism on Cisco network devices (routers, switches etc) which is mainly used for traffic filtering.
In this article we will examine a different type of ACL, called the Vlan Access Control List (VACL) which works a little different from the classic ACL.
In any network setup you need to have full control on traffic that enters and leaves your network. Most of the times we use filtering to permit or deny specific routed traffic from one Layer3 subnet to another Layer3 subnet.
Usually this type of filtering is controlled by ACLs which filter routed traffic (i.e traffic between different Layer3 networks).
What if we want to control traffic flow within the same VLAN (and hence, within the same Layer3 network)? This can be achieved using a VACL which can block or permit traffic flow within the same VLAN.
VACLs are supported on Cisco Layer3 switches. In this tutorial we will examine two simple filtering examples:
- Traffic filtering on a Layer3 switch using classic ACL for traffic control between layer3 networks.
- Traffic filtering on a Layer3 switch using Vlan ACL (VACL) for traffic control within the same layer3 network (vlan).
For more information about Layer3 switches and inter-vlan routing see this post HERE.
Let’s start with our first example:
1. Traffic Filtering Using classic ACL on Cisco Layer3 switch
As you have learned in CCNA you can filter traffic using an ACL that can be either:
- Standard ACL: Contains only source IP address.
- Extended ACL: Contains both source/destination IPs and ports.
*filtering can also be done using prefix-lists and route-maps but it’s not the objective of this tutorial.
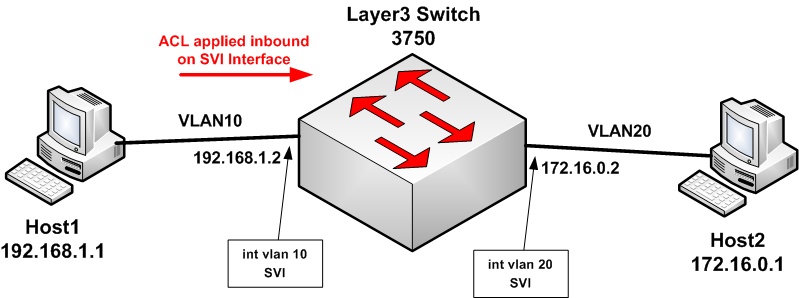
In this first simple ACL filtering example, the requirement is to block telnet traffic from Host1 to Host2. To achieve this, we will use an extended ACL applied inbound on one of the Switch VLAN Interfaces (SVI) (vlan 10) of the Layer3 switch as shown below.
First let’s verify connectivity between the hosts before applying the ACL:
H1#ping 172.16.0.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.0.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
H1#telnet 172.16.0.1
Trying 172.16.0.1 … Open
User Access Verification
Username:
As shown above, we have connectivity between the two hosts. To demonstrate how you can use ACL filtering, I will block the telnet session from Host1 to Host2 using an ACL applied inbound on the SVI interface for VLAN10 of the switch.
NOTE:
An ACL applied inbound on the SVI interface (interface vlan 10) blocks traffic coming from hosts connected to VLAN10 ports towards the switch.
Configuration on the switch that will block telnet from Host1 to Host2.
- Configure ACL on the switch to block telnet
ip access-list extended Block_Telnet
deny tcp host 192.168.1.1 host 172.16.0.1 eq 23
permit ip any any < —- permit all other traffic
- Apply the ACL to the SVI Interface of the switch
interface Vlan10 < —- This is the first SVI of the Layer3 switch for VLAN10
description to Host1
ip address 192.168.1.2 255.255.255.0
ip access-group Block_Telnet in < — Apply the ACL inbound to filter traffic that comes in the SVI from Host1
interface Vlan20 < —- This is the second SVI of the Layer3 switch for VLAN20 (no ACL on this one)
description to Host2
ip address 172.16.0.2 255.255.255.0
- Verification
H1#telnet 172.16.0.1
Trying 172.16.0.1 ….
% Connection timed out; remote host not responding
As you can see, telnet traffic has been blocked.
2. Traffic Filtering Using VACL on a Cisco Layer3 switch
An ACL is using source and/or destination IPs and ports to directly match packets that are to be filtered.
A VACL on the other hand is used in switched networks where you want to filter traffic within the VLAN. VACLs are similar in logic with route maps but instead of “route-map” entries they contain “access-map” entries.
Each “access-map” entry contains a match statement (using a normal ACL) and forward or drop actions accordingly.
You can have different matching statements for every access-map sequence and they will be processed in the order they are entered.
Just like a normal route map, there is an implicit deny-all statement at the end so make sure to create a final access-map entry which permits all other traffic.
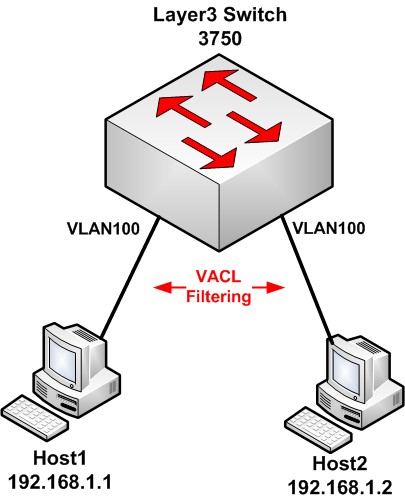
As shown on the diagram, we have two hosts in the same VLAN 100 (and same Layer3 subnet 192.168.1.0/24) connected on the same Layer3 switch. We want to restrict telnet access from Host1 to Host2.
First let’s verify connectivity between the two hosts without the VACL applied:
H1#ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
H1#telnet 192.168.1.2
Trying 192.168.1.2… Open
User Access Verification
Username:
Configuration of VACL on the switch to block telnet from Host1 to Host2
- Configure an ACL to match telnet traffic from Host1 to Host2.
SW1(config)#ip access-list extended Block_Telnet
SW1(config-ext-nacl)#permit tcp host 192.168.1.1 host 192.168.1.2 eq 23
SW1(config-ext-nacl)#exit
- Configure the Vlan Access Map aka VACL
SW1(config)#vlan access-map VACL_ Block_Telnet 10 < —- First VACL entry
SW1(config-access-map)#action drop < —- sets the action to drop
SW1(config-access-map)#match ip address Block_Telnet < — matches the ACL configured above
SW1(config-access-map)#vlan access-map VACL_ Block_Telnet 20 < —- Second VACL entry
SW1(config-access-map)#action forward < —- permits all other traffic
SW1(config-access-map)#exit
IMPORTANT
The configuration above might look confusing. The ACL in Step1 contains a “permit” statement for telnet traffic between Host1 to Host2. This DOES NOT mean that we permit telnet. The “permit” statement is used to match telnet traffic from Host1 to Host2 and then drop that traffic inside the VACL access-map with the “action drop” command (see Step2).
- Apply the VACL on the VLAN
SW1(config)#vlan filter VACL_ Block_Telnet vlan-list 100
Verification
H1#ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
H1#telnet 192.168.1.2
Trying 192.168.1.2…
% Connection timed out; remote host not responding
Telnet on another port works fine
H1#192.168.1.2 80
Trying 192.168.1.2, 80 … Open
VACL vs ACL
After configuring both VACL and ACL in this article you should have figured out already the differences between the two.
Let’s summarize them below:
- VACL is a Layer 2 concept. It can be applied on a VLAN to restrict and control traffic flow on hosts within the same Layer 2 VLAN on intra-VLAN (i.e same subnet).
- ACL on the other hand is a Layer 3 concept. An Access Control List (ACL) controls Layer 3 traffic between different VLANs/subnets (Layer 3 networks). So it works on inter-VLAN traffic.
DOWNLOAD ARTICLE AS PDF FILE
Related Posts
- How Does a Network Switch Learn MAC Addresses?
- How to Find a Device MAC Address on a Cisco Switch (show mac address-table)
- How to Configure a Loopback Interface on Cisco Router & Switch
- Cisco Switch Layer2 Layer3 Design and Configuration
- Description of Switchport Mode Access vs Trunk Modes on Cisco Switches