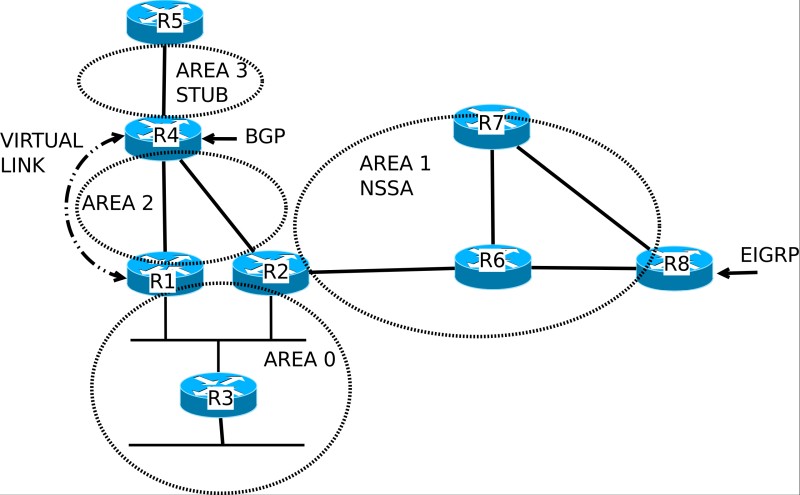
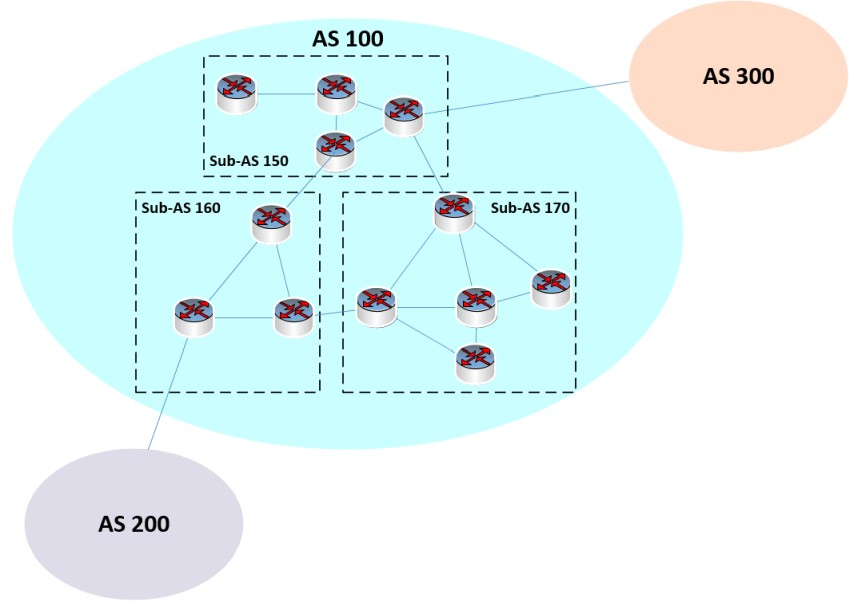
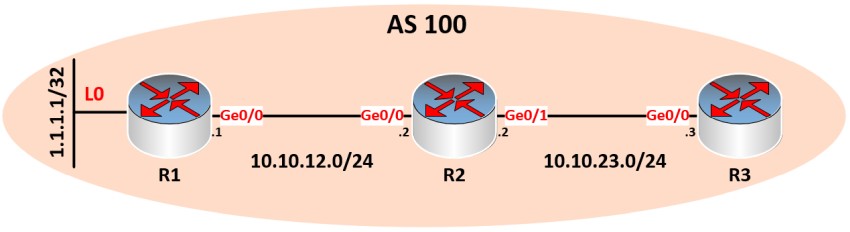
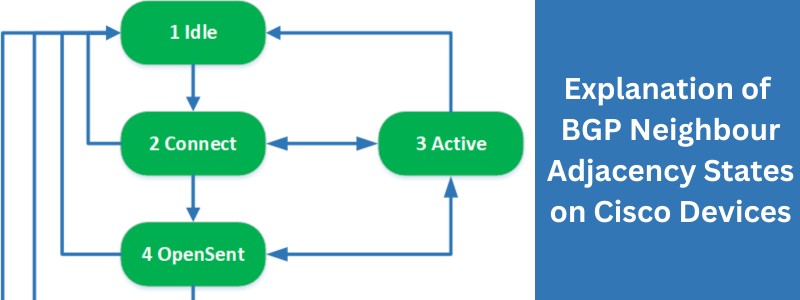
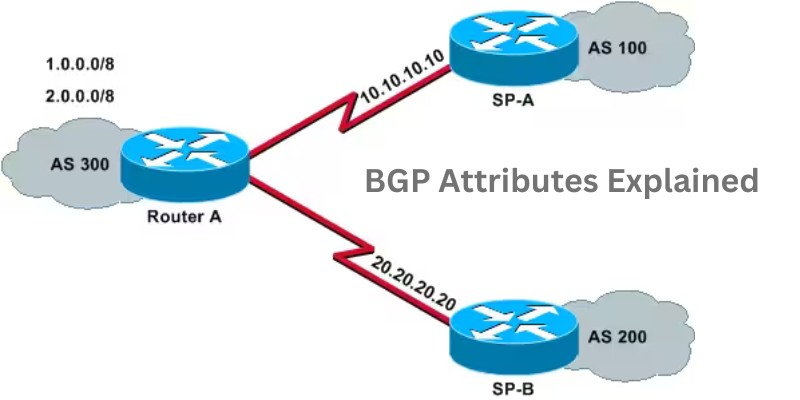
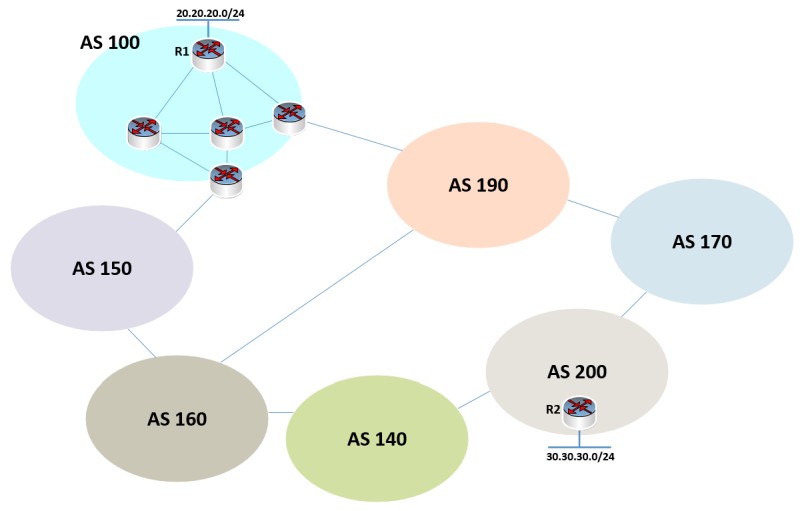
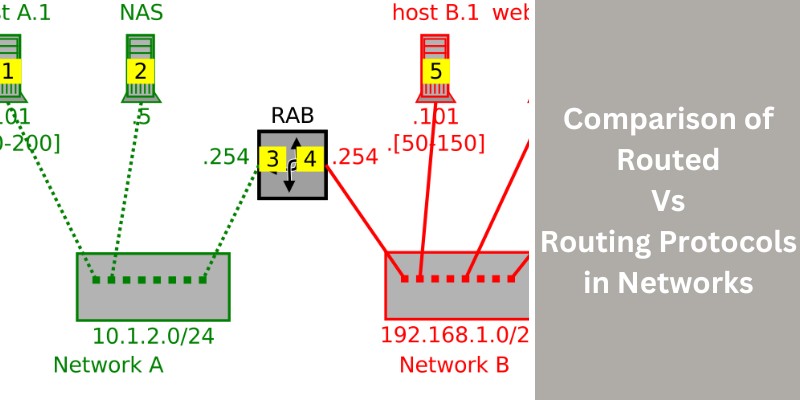
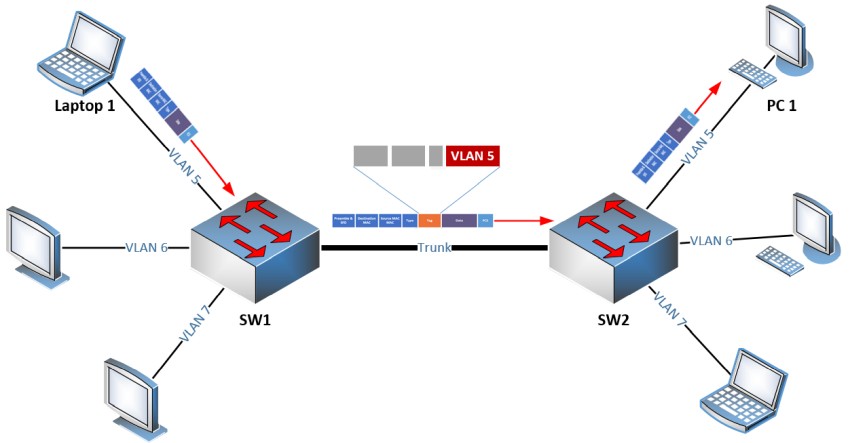
Although I have been a TCP/IP networking professional for decades, in the last 10 years I’m also involved in network security as well. One of the tasks I’m responsible to do in my work environment is to either coordinate or perform network assessment projects on my own. A major part of a network security assessment […]
[Continue reading]