A “Firewall” is one of the most popular computer and network security devices that professionals use to protect their enterprise IT assets and networks.
Just like a fire-resistant door in buildings which protects rooms from a possible fire and stops the spreading of flames within the building, the security firewall has a similar function to prevent malicious packets and traffic from entering and harming your protected computer assets.
In this website I have written hundreds of articles around Cisco ASA firewalls, which represent a classic example of hardware network-based firewalls.
However, there are also other types of firewalls such as host-based firewalls which we’ll also discuss and compare in this post.
What is a Network based Firewall
As the name implies, this type of firewall is mainly used to protect whole computer networks from attacks and also for controlling network traffic so that only allowed packets are able to reach your servers and IT assets.

The picture above shows several Cisco ASA network-based firewalls. As you can see, these are hardware devices containing several Ethernet ports for connecting to a network (ranging from SMB to large Enterprise Networks).
These ports are usually 1 Gbps ports with electrical RJ45 connectors but you can find also optical ports (e.f 1 Gbps, 10 Gbps speed ports etc) for connecting to fiber optic cables for longer distances and larger bandwidth.
The physical ports of a network firewall are connected to network switches in order to implement the firewall within the LAN network.
In its simplest form, you can connect several physical ports of the firewall to different network switches in order to provide controlled access between different network segments.
The most popular use case of a network-based firewall is when it is used as Internet border device to protect a company’s LAN from the Internet as shown in the diagram below:
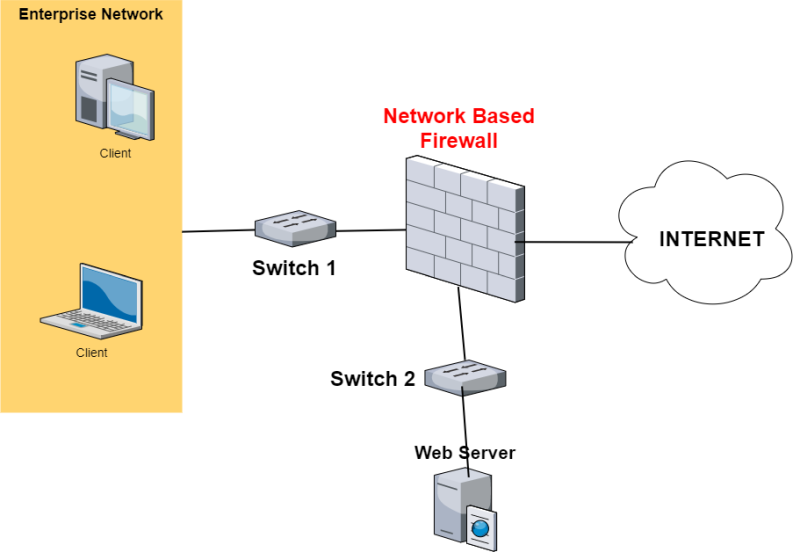
The network above is one of the most popular use-cases of network firewalls as used in enterprise networks. As you can see, one port of the firewall is connected to the network Switch-1 which accommodates all of the LAN client devices of the Enterprise Network.
Another physical port of the firewall is connected to a different network Switch-2 which connects to a Web Server.
Therefore, in the scenario above we have managed to separate the publicly accessible Web Server from the rest of the Enterprise Network via the security appliance. This is a good security practice because if the Web Server gets compromised by a hacker, there will not be any access to the protected internal secure network.
The firewall must be configured to allow traffic from Internet towards the Web Server at a specific TCP port (port 443 for HTTPs or port 80 for HTTP).
All other traffic will be blocked by the firewall (i.e no direct traffic from the Internet towards the internal Enterprise Network will be allowed).
Moreover, the firewall will allow also outgoing traffic from the Enterprise Network towards the Internet in order to provide Internet access to internal LAN hosts.
As described in the above use-case, the network firewall is responsible for allowing or denying network packets between networks (using OSI Layer 3 and Layer 4 access rules). This is the most basic functionality of the firewall.
Newest generations of firewalls (called “Next Generation Firewalls”) also inspect traffic at the application layer to identify malicious traffic and attacks at the application level (e.g viruses, intrusion attempts, SQL injection attacks etc etc).
What is a Host based Firewall
As the name implies, a host-based firewall is a software application installed on host computers or servers to protect them from attacks.
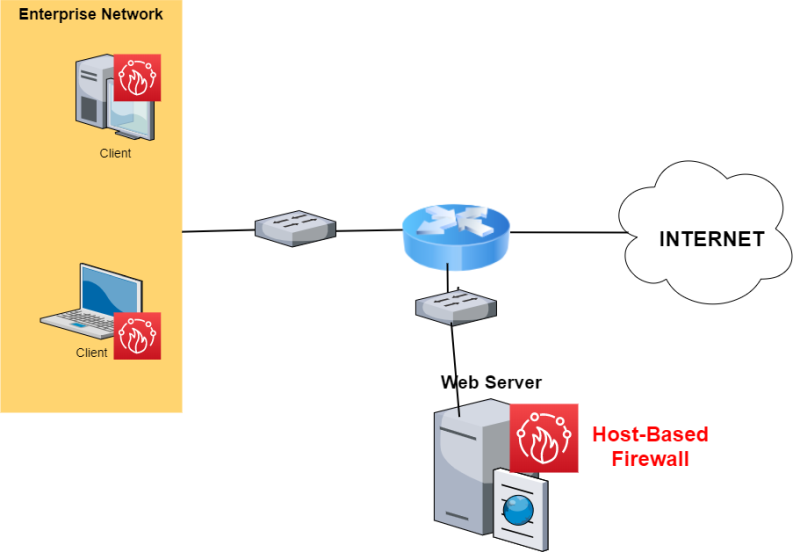
Although the network depicted above is not recommended in real scenarios, it illustrates how a host-based firewall is used.
Note that the best option would be to combine both a network firewall and host-firewalls for better protection using a layered-approach.
The Host-based firewall is directly installed as software on the host and controls incoming and outgoing traffic to and from the specific host.
A classic example of host firewall is the Windows Firewall which comes by default in all Windows Operating Systems.
Because this type of protection is bound to the host itself, it means that it provides protection to the host no matter which network is connected to.
For example, if you are connected to your enterprise network, you are already protected by your network firewall. Now, if you take your laptop with a host-based firewall and connect it to an external WiFi network, the firewall still provides protection to the computer.
Moreover, some host-based firewalls provide also protection against application attacks. Since this type of protection is installed on the actual host, it has visibility on the applications and processes running on the host, therefore the firewall can protect against malware that try to infect the system.
One weak point of such a firewall is that it can be turned-off by an attacker who managed to gain admin level access to the host.
If the host is compromised by a hacker with administrator privileges, the host-based firewall can be turned-off, something that is impossible to do on network-based firewalls.
Comparison between Network Based and Host Based Firewalls
| Characteristics | Network Firewall | Host Firewall |
| Placement | Inside the network (either at the border/perimeter or inside the LAN) | On each host |
| Hardware/Software | Hardware Device | Software Application |
| Performance | High performance (bandwidth, concurrent connections etc) | Lower performance (since it is software based) |
| Level of protection | Network protection plus Application level protection (if using Next Generation Firewall) | Network protection plus Application protection (on some models) |
| Use-cases | Mostly in Enterprise Networks | Both in personal computers in home networks and also in Enterprise networks as additional protection on hosts. |
| Network Segmentation | Great segmentation and control at the VLAN / Layer 3 level but can’t restrict traffic between hosts in the same VLAN | Great micro-segmentation at the host level even if the hosts belong in the same VLAN. |
| Mobility | Once firewall is implemented inside the network, it is very hard to remove or change. | High mobility since it is bound to each host. |
| Management | Can be managed from a central firewall management server or directly on the appliance itself | Hard to manage when hundreds of hosts exist in the network. |
| How easy to Bypass | Network firewalls can’t be bypassed by attackers. | Easier to bypass. If the attacker compromises the host via an exploit, the firewall can be turned-off by the hacker. |
Related Posts
- 5 Best Practices to Keep Rogue Devices at Bay
- Cisco Talos Year in Review – Top Cyber Security Threats in 2023 and Beyond
- How to Scan an IP Network Range with NMAP (and Zenmap)
- What is Cisco Identity Services Engine (ISE)? Use Cases, How it is Used etc
- What is Cisco Umbrella Security Service? Discussion – Use Cases – Features