Dynamic Multipoint VPN (DMVPN) is a Cisco VPN solution used when high scalability and minimal configuration complexity is required in connecting branch offices to a central HQ Hub site.
DMVPN is one of the most scalable and most efficient VPN types supported by Cisco. It is used almost exclusively with Hub-and-Spoke topologies where you want to have direct Spoke-to-Spoke VPN tunnels in addition to the Spoke-to-Hub tunnels. This means that Spoke sites can communicate between them directly without having to go through the Hub. DMVPN is supported only on Cisco Routers.
If you want to design a VPN solution to connect numerous sites between them (I would say more than 10 sites), then DMVPN using Cisco routers is an ideal choice. Although the most common topology is Hub-and-spoke setup, DMVPN supports full mesh connectivity since all sites can communicate between them without having to configure static VPN tunnels between each other.
Some characteristics of DMVPN are the following:
- The HUB central router acts as the DMVPN server and the Spoke routers (in branch offices) act as the DMVPN clients.
- The HUB router must have static public IP address on its WAN interface.
- The spoke branch routers can have either static or dynamic public IP on the WAN.
- Each branch site (Spoke) has a permanent IPSECTunnel with the Central site (Hub).
- The Spoke-to-Spoke tunnels are established on demand whenever there is traffic between the Spoke sites. Thereafter, packets are able to bypass the Hub site and use the spoke-to-spoke tunnel directly.
- All tunnels are using Multipoint GREwith IPSEC
- NHRP(Next Hop Resolution Protocol) is used to map the private IPs of Tunnel Interfaces with their corresponding WAN Public IPs.
- The above NHRPmappings will be kept on the NHRP Server router (HUB). Each Spoke communicates with the NHRP Server (Hub) and registers its public IP address and its private Tunnel Interface IP to the Hub router. Thus, the Hub router will store all mappings for “Tunnel Interface IP / Public WAN IP” of all the Spoke sites.
- When a spoke needs to send a packet to a destination (private) subnet on another spoke, it queries the NHRPserver in order to learn the public (outside WAN) address of the destination (target) spoke.
- For better scalability, it is recommended to run a dynamic routing protocols (such as EIGRP) between all the routers.
DMVPN uses the following group of networking technologies
- Multipoint GRE
- IPSEC
- Next-Hop Resolution Protocol – NHRP
- Static or dynamic routing
Configuration example
In this Cisco DMVPN configuration example we present a Hub and Spoke topology with a central HUB router that acts as a DMVPN server and 2 spoke routers that act as DMVPN clients.
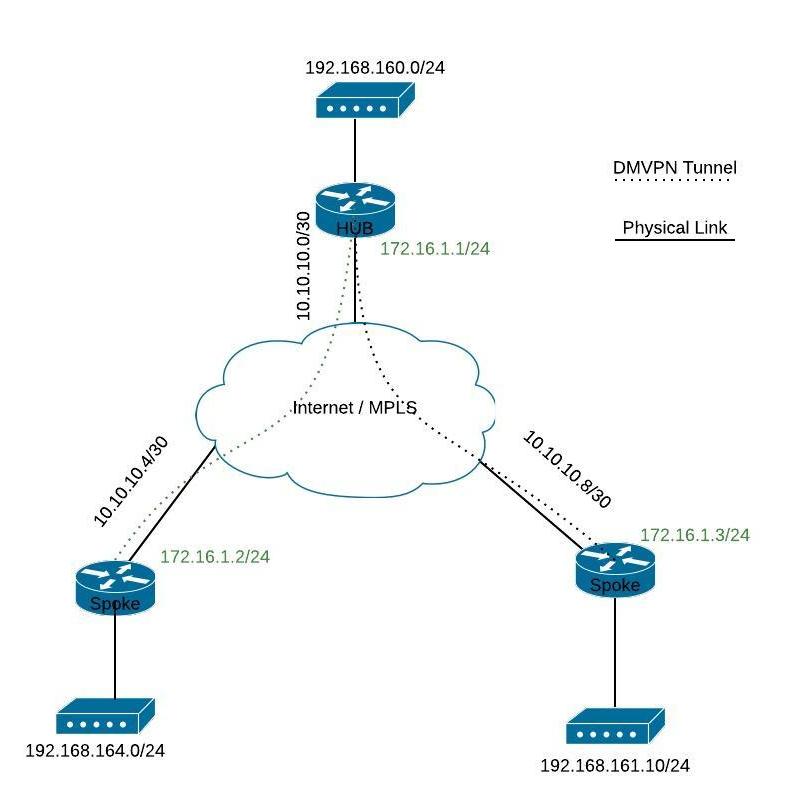
All the routers involved in this tutorial are CISCO1921/K9
Step 1. Configure the HUB router
The hub router requires a static IP configured on the WAN interface facing the internet.
! Interface Configuration
interface GigabitEthernet0/0
description to Internet-WAN
ip address 10.10.10.1 255.255.255.252
!
interface GigabitEthernet0/1
description to LAN
ip address 192.168.160.1 255.255.255.0
duplex auto
! Configure the tunnel interface , which basically is an enhanced GRE tunnel (Multipoint GRE)
interface Tunnel1
description DMVPN Tunnel
ip address 172.16.1.1 255.255.255.0 < — Select a private IP subnet for the tunnels
no ip redirects
ip nhrp authentication nhrp1234 < —– authentication used for updates between the routers
ip nhrp network-id 1 < — Network identification that has to be the same on all the routers
load-interval 30
keepalive 5 10
tunnel source GigabitEthernet0/0 < — source of the tunnel is the WAN interface
tunnel mode gre multipoint < —— designates the tunnel as a mGRE tunnel
tunnel protection ipsec profile protect-gre < —– encrypts the traffic passing through this tunnel using ipsec
ip mtu 1440 < —-Reduce the MTU to allow extra overhead from mGRE and IPSEC
ip nhrp map multicast dynamic < — Enables forwarding of multicast traffic across the tunnel.
! Configure IPSEC on HUB
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key isakmp1234 address 0.0.0.0 0.0.0.0 —- > accept connection from any source to accommodate also dynamic spokes
!
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
mode tunnel
!
!
crypto ipsec profile protect-gre ——– > profile added to the mGRE tunnel for encryption
set security-association lifetime seconds 86400
set transform-set TS
! Configure static routing on HUB (dynamic routing is recommended for larger networks)
ip route 192.168.164.0 255.255.255.0 172.16.1.2 < —The remote LAN can be reached via the remote tunnel IP
ip route 192.168.161.0 255.255.255.0 172.16.1.3 < —The remote LAN can be reached via the remote tunnel IP
Step 2 . Configure the Spoke Routers
One of the routers has DHCP assigned IP on WAN and the other one has static WAN IP.
Spoke 1 (Dynamic IP assigned from DHCP)
interface GigabitEthernet0/0
description WAN to Internet
ip address dhcp
duplex auto
speed auto
interface GigabitEthernet0/1
description To LAN
ip address 192.168.164.1 255.255.255.0
duplex auto
speed auto
interface Tunnel1
ip address 172.16.1.2 255.255.255.0 < —in same subnet as all the other tunnels
no ip redirects
ip nhrp map multicast dynamic < — Enables forwarding of multicast traffic across the tunnel.
tunnel source GigabitEthernet0/0 < — source is WAN interface
tunnel mode gre multipoint
tunnel protection ipsec profile protect-gre
ip nhrp authentication nhrp1234
ip nhrp map 172.16.1.1 10.10.10.1 —– > maps the tunnel IP address of the HUB to the WAN IP of the HUB that has to be static
ip nhrp network-id 1
ip nhrp nhs 172.16.1.1 —— > configures NHRP client with the IP address of its NHRP server
ip nhrp registration no-unique —– > if a NHRP map is done for this IP another one will not be allowed
ip nhrp map multicast 10.10.10.1 < — Send multicast traffic to the Hub only. Hub will receive all multicast traffic (e.g routing protocol updates) and then send out updates to all the Spoke routers.
ip mtu 1440
load-interval 30
keepalive 5 10
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key isakmp1234 address 0.0.0.0 0.0.0.0 < —Spoke routers must allow also connections from any IP in order to form IPSEC VPN tunnels with other Spokes.
!
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
mode tunnel
!
crypto ipsec profile protect-gre
set security-association lifetime seconds 86400
set transform-set TS
ip route 192.168.160.0 255.255.255.0 172.16.1.1 < –Route for HUB
ip route 192.168.161.0 255.255.255.0 172.16.1.3 < –Route for other Spoke site
Spoke 2 (Static IP on WAN)
interface GigabitEthernet0/0
description TO Internet
ip address 10.10.10.9 255.255.255.252
duplex auto
speed auto
interface GigabitEthernet0/1
description To: LAN
ip address 192.168.161.1 255.255.255.0
duplex auto
speed auto
interface Tunnel1
ip address 172.16.1.3 255.255.255.0 < –in same subnet as all the other tunnels
no ip redirects
ip nhrp map multicast dynamic < — Enables forwarding of multicast traffic across the tunnel.
tunnel source GigabitEthernet0/0
tunnel mode gre multipoint
tunnel protection ipsec profile protect-gre
ip nhrp authentication nhrp1234
ip nhrp map 172.16.1.1 10.10.10.1 —– > maps the tunnel IP address of the HUB to the WAN IP of the HUB that has to be static
ip nhrp network-id 1
ip nhrp nhs 172.16.1.1 —— > configures NHRP client with the IP address of its NHRP server
ip nhrp registration no-unique —– > if a NHRP map is done for this IP another one will not be allowed
ip nhrp map multicast 10.10.10.1 < — Send multicast traffic to the Hub only. Hub will receive all multicast traffic (e.g routing protocol updates) and then send out updates to all the Spoke routers.
ip mtu 1440
load-interval 30
keepalive 5 10
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key isakmp1234 address 0.0.0.0 0.0.0.0 < —Spoke routers must allow also connections from any IP in order to form IPSEC VPN tunnels with other Spokes.
!
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
mode tunnel
!
!crypto ipsec profile protect-gre
set security-association lifetime seconds 86400
set transform-set TS
ip route 192.168.160.0 255.255.255.0 172.16.1.1 < –Route for HUB
ip route 192.168.164.0 255.255.255.0 172.16.1.2 < –Route for other Spoke site
Step 3 – Verify the DMVPN on the HUB
show dmvpn
Legend: Attrb –> S – Static, D – Dynamic, I – Incomplete
N – NATed, L – Local, X – No Socket
T1 – Route Installed, T2 – Nexthop-override
C – CTS Capable
# Ent –> Number of NHRP entries with same NBMA peer
NHS Status: E –> Expecting Replies, R –> Responding, W –> Waiting
UpDn Time –> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel1, IPv4 NHRP Details
Type:Hub, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
—– ————— ————— —– ——– —–
1 10.10.10.5 (peer public IP) 172.16.1.2 (peer tunnel IP ) UP 07:51:19 D
2 10.10.10.9 172.16.1.3 UP 09:41:33 D
show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
10.10.10.5 10.10.10.1 QM_IDLE 1011 ACTIVE —— > IPsec connectivity between routers
10.10.10.9 10.10.10.1 QM_IDLE 1012 ACTIVE
HUB# ping 192.168.164.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.164.1, timeout is 2 seconds:
.!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms
HUB# ping 192.168.161.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.161.1, timeout is 2 seconds:
.!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms
Note : You can use either static routing or a dynamic routing protocol for enabling communication in the DMVPN cloud. In this tutorial we have used static routing but for larger networks you should enable dynamic routing such as EIGRP
DOWNLOAD ARTICLE AS PDF FILE
Related Posts
- VPN Failover with HSRP High Availability (Crypto Map Redundancy)
- Cisco IPsec Tunnel vs Transport Mode with Example Config
- Site to Site IPSEC VPN Between Cisco Router and Juniper Security Gateway
- Site-to-Site IPSEC VPN Between Cisco ASA and pfSense
- Site-to-Site IPSEC VPN Between Two Cisco ASA – one with Dynamic IP