This Cisco ASA Tutorial gets back to the basics regarding Cisco ASA firewalls. I’m offering you here a basic configuration tutorial for the Cisco ASA 5510 security appliance but the configuration applies also to the other ASA models as well (see also this Cisco ASA 5505 Basic Configuration).
The 5510 ASA device is the second model in the ASA series (ASA 5505, 5510, 5520 etc) and is fairly popular since it is intended for small to medium enterprises.
Like the smallest ASA 5505 model, the 5510 comes with two license options: The Base license and the Security Plus license.
The second one (security plus) provides some performance and hardware enhancements over the base license, such as 130,000 Maximum firewall connections (instead of 50,000), 100 Maximum VLANs (instead of 50), Failover Redundancy, etc.
Also, the security plus license enables two of the five firewall network ports to work as 10/100/1000 instead of only 10/100.
Next we will see a simple Internet Access scenario which will help us to understand the basic steps needed to setup an ASA 5510.
Assume that we are assigned a static public IP address 100.100.100.1 from our ISP. Also, the internal LAN network belongs to subnet 192.168.10.0/24.
Interface Ethernet0/0 will be connected to the outside (towards the ISP), and Ethernet0/1 will be connected to the Inside LAN switch. Refer to the diagram below for our example scenario.
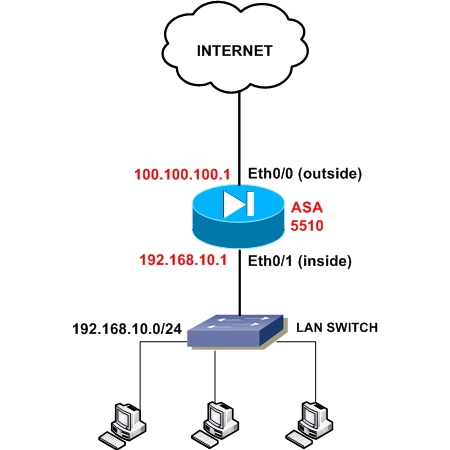
The firewall will be configured to supply IP addresses dynamically (using DHCP) to the internal hosts. All outbound communication (from inside to outside) will be translated using Port Address Translation (PAT) on the outside public interface. Let’s see a snippet of the required configuration steps for this basic scenario:
Step1: Configure a privileged level password (enable password)
By default there is no password for accessing the ASA firewall, so the first step before doing anything else is to configure a privileged level password, which will be needed to allow subsequent access to the appliance. Configure this under Configuration Mode:
ASA5510(config)# enable password mysecretpassword
Step2: Configure the public outside interface
ASA5510(config)# interface Ethernet0/0
ASA5510(config-if)# nameif outside
ASA5510(config-if)# security-level 0
ASA5510(config-if)# ip address 100.100.100.1 255.255.255.252
ASA5510(config-if)# no shut
Step3: Configure the trusted internal interface
ASA5510(config)# interface Ethernet0/1
ASA5510(config-if)# nameif inside
ASA5510(config-if)# security-level 100
ASA5510(config-if)# ip address 192.168.10.1 255.255.255.0
ASA5510(config-if)# no shut
Step 4: Configure PAT on the outside interface
ASA5510(config)# global (outside) 1 interface
ASA5510(config)# nat (inside) 1 0.0.0.0 0.0.0.0
UPDATE for ASA Version 8.3 and later (including ASA 9.x)
From March 2010, Cisco announced the new Cisco ASA software version 8.3. This version introduced several important configuration changes, especially on the NAT/PAT mechanism.
The “global” command is no longer supported. NAT (static and dynamic) and PAT are configured under network objects. The PAT configuration below is for ASA 8.3 and later:
object network obj_any
subnet 0.0.0.0 0.0.0.0
nat (inside,outside) dynamic interface
Step 5: Configure Default Route towards the ISP (assume default gateway is 100.100.100.2)
ASA5510(config)# route outside 0.0.0.0 0.0.0.0 100.100.100.2 1
Step 6: Configure the firewall to assign internal IP and DNS address to hosts using DHCP
ASA5510(config)# dhcpd dns 200.200.200.10
ASA5510(config)# dhcpd address 192.168.10.10-192.168.10.200 inside
ASA5510(config)# dhcpd enable inside
The above basic configuration is just the beginning for making the appliance operational. There are many more configuration features that you need to implement to increase the security of your network, such as Static and Dynamic NAT, Access Control Lists to control traffic flow, DMZ zones, VPN etc.
I just tried to offer you a starting point for a basic configuration from where you can build your knowledge further. For a more complete practical guide about Cisco ASA Firewall configuration I suggest you to read the “Cisco ASA Firewall Fundamentals – 3rd Edition” ebook at the link HERE.
DOWNLOAD THIS ARTICLE AS PDF FILE
Related Posts
- Prevent Spoofing Attacks on Cisco ASA using RPF
- Configuring Connection Limits on Cisco ASA Firewalls – Protect from DoS
- Configuring AAA Authentication-Authorization-Accounting on Cisco ASA Firewall (TACACS+, RADIUS)
- Cisco ASA Firewall Management Interface Configuration (with Example)
- How to Configure Access Control Lists on a Cisco ASA 5500/5500-X Firewall (with Examples)