A wildcard mask is a bitmask used with IPv4 to specify ranges of IP addresses, which are then leveraged by various features, including access control lists and routing protocols.
There’s a lot more to wildcard masks than meets the eye, and they’re a lot more powerful than you may initially think. In this article, we’ll dive deeper into what they are and how they can be used in various ways.
What is a wildcard mask?
A wildcard mask is composed of a series of 32 bits and functions similarly to a subnet mask but in the opposite way.
Where a subnet mask uses binary 1s to represent network bits and binary 0s to represent host bits, a wildcard mask will use 1s for host bits and 0s for network bits.
For example, if you have an IP network address of 192.168.1.0 and want to define a range of addresses from 192.168.1.0 to 192.168.1.255, you would use a subnet mask of 255.255.255.0.
The 255.255.255.0 subnet mask is represented like so in binary:
11111111.11111111.11111111.00000000
If you were to use the corresponding wildcard mask to define the same range, you would have to use the opposite, which in binary is:
00000000.00000000.00000000.11111111
And in dotted decimal format, this translates to 0.0.0.255
So, a notation using a wildcard mask of 192.168.1.0 0.0.0.255 specifies the range of addresses from 192.168.1.0 to 192.168.1.255.
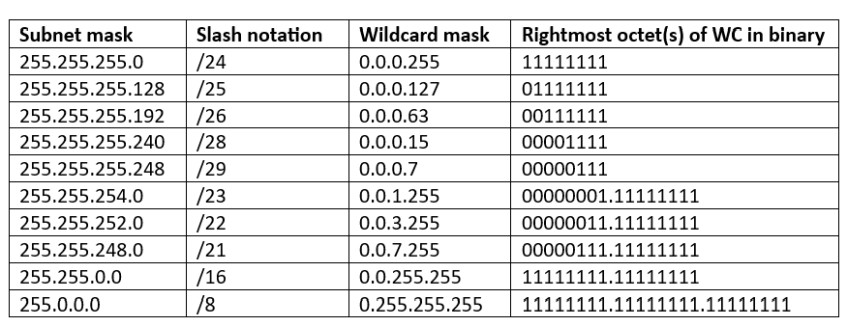
The following table shows some of the most common subnet masks and their wildcard mask counterparts in dotted decimal format. The slash notation is also included as well as the rightmost octets of the wildcard mask in binary.
| Subnet mask | Slash notation | Wildcard mask | Rightmost octet(s) of WC in binary |
| 255.255.255.0 | /24 | 0.0.0.255 | 11111111 |
| 255.255.255.128 | /25 | 0.0.0.127 | 01111111 |
| 255.255.255.192 | /26 | 0.0.0.63 | 00111111 |
| 255.255.255.240 | /28 | 0.0.0.15 | 00001111 |
| 255.255.255.248 | /29 | 0.0.0.7 | 00000111 |
| 255.255.254.0 | /23 | 0.0.1.255 | 00000001.11111111 |
| 255.255.252.0 | /22 | 0.0.3.255 | 00000011.11111111 |
| 255.255.248.0 | /21 | 0.0.7.255 | 00000111.11111111 |
| 255.255.0.0 | /16 | 0.0.255.255 | 11111111.11111111 |
| 255.0.0.0 | /8 | 0.255.255.255 | 11111111.11111111.11111111 |
The context in which you use the range of IP addresses will determine whether you must use a subnet mask or wildcard mask.
What features use wildcard masks?
The most common feature on a Cisco IOS device that uses wildcard masks is access control lists (ACLs), both standard and extended.
Other than ACLs, however, many more features leverage wildcard masks. These include:
- Routing protocols such as OSPF, EIGRP and BGP
- Route maps
- IP summarization
- Network Address Translation (NAT)
- Virtual Routing and Forwarding (VRFs)
As you can see, there are a lot of features and constructs that leverage wildcard masks to define ranges of IP addresses.
Note that each feature may use wildcard masks slightly differently, and you should learn how to use them within the context of each feature.
But there is another issue that we should keep in mind as well. Some of these features will accept a subnet mask instead of a wildcard mask.
Routing protocols such as EIGRP and OSPF are features that can use either a wildcard mask or a subnet mask when defining the subnets that will be participating in the routing protocol. This is typically done to make it easier for administrators.
Which feature accepts wildcard masks, which accepts subnet masks, and which accepts both can differ from platform to platform and from IOS version to IOS version, so you should check either Cisco command reference documentation or experiment directly yourself.
Examples of the use of wildcard masks
The following sections contain examples of how wildcard masks are used with various features found within Cisco IOS devices.
Access control list
A wildcard mask is used in ACLs to specify IP address ranges for permitting or denying traffic. Here are two examples of how wildcard masks can be used in ACL configurations:
Example 1 – Permit traffic from a specific subnet:
ip access-list extended ACL-Example1
permit ip 192.168.1.0 0.0.0.127 any
In this example, the wildcard mask 0.0.0.127 is used to represent the IP address range 192.168.1.0 – 192.168.1.127 (192.168.1.0/25 subnet).
The ACL permits traffic from any host within this subnet to any destination. For reference, the wildcard mask in binary form looks like this:
00000000.00000000.00000000.01111111
Example 2 – Deny traffic from a specific host:
ip access-list extended ACL-Example2
deny ip host 10.0.0.5 any
permit ip any any
In this example, the “host” keyword is used as a shorthand for a wildcard mask of 0.0.0.0, which specifies an exact match for the IP address 10.0.0.5. The ACL denies traffic from this specific host to any destination while permitting all other traffic.
EIGRP
A wildcard mask is used in EIGRP configurations to identify which interfaces should participate in the EIGRP routing process. Here’s an example of how a wildcard mask can be used in an EIGRP configuration:
Let’s say you have a router with the following interfaces and IP addresses:
- FastEthernet0/0: 192.168.0.1/23
- FastEthernet0/1: 192.168.2.1/23
You want to configure EIGRP to include only the FastEthernet0/0 interface (192.168.0.0/23 subnet) in the routing process. You would use the following configuration:
router eigrp 100
network 192.168.0.0 0.0.1.255
In this example, the EIGRP process with AS number 100 is configured with a network statement that includes the IP address range 192.168.0.0 – 192.168.1.255, using the wildcard mask 0.0.1.255. This wildcard mask looks like this in binary:
00000000.00000000.00000001.11111111
As a result, only the FastEthernet0/0 interface, which has an IP address within the specified range, will participate in the EIGRP process.
Network Address Translation
Wildcard masks can be used with NAT on Cisco routers to define the IP address ranges that should be translated. Here’s an example of how a wildcard mask can be used in a NAT configuration:
Let’s say you have a router with the following interfaces and IP addresses:
- FastEthernet0/0 (inside interface): 192.168.1.1/24
- FastEthernet0/1 (outside interface): 203.0.113.2/29
You want to configure dynamic NAT to translate the internal IP addresses (192.168.1.0/24 subnet) to the available public IP addresses in the 203.0.113.2/29 subnet. You would use the following configuration:
- Define an access list using a wildcard mask to match the inside IP address range:
access-list 1 permit 192.168.1.0 0.0.0.255
In this example, the access list matches the IP address range 192.168.1.0 – 192.168.1.255, using the wildcard mask 0.0.0.255.
- Create a NAT pool containing the available public IP addresses:
ip nat pool PublicPool 203.0.113.3 203.0.113.6 netmask 255.255.255.248
- Configure dynamic NAT using the access list and NAT pool:
ip nat inside source list 1 pool PublicPool
- Apply the NAT configuration to the appropriate interfaces:
interface FastEthernet0/0
ip nat inside
interface FastEthernet0/1
ip nat outside
In this example, the wildcard mask is used in the access list to specify the IP address range of the internal network that should be translated using dynamic NAT.
The NAT configuration allows the internal hosts to share the public IP addresses in the NAT pool when accessing resources outside the local network.
Can a subnet mask do this?
One final thought that I’m sure has gone through your head. Why use wildcard masks at all when we can use subnet masks?
Wildcard masks and subnet masks both serve important purposes in different scenarios, but they are not always interchangeable. Wildcard masks provide flexibility and granularity in certain configurations that subnet masks cannot provide.
Where subnet masks must have their 1s and 0s arranged in a contiguous manner, wildcard masks can have any combination of 1s and 0s, even non-contiguously.
This will become clearer in the examples that follow. This way, wildcard masks can represent non-contiguous IP address ranges with a single statement that cannot be defined using subnet masks.
Simple Non-contiguous example
For example, let’s say I want to define an access list that will permit only two source IP addresses, specifically 192.168.1.5 and 192.168.1.7, and will deny all others. We can achieve this with a single statement within the ACL:
ip access-list extended NonContiguousACL1
permit ip 192.168.1.5 0.0.0.2 any
deny ip any any
That might look strange to you, but it will work. Let’s do the math. Here are the addresses we want to match in binary:
192.168.1.5 in binary is 11000000.10101000.00000001.00000101
192.168.1.7 in binary is 11000000.10101000.00000001.00000111
Notice that the only difference is the second to last bit, which is in red bold. The rest remain the same. For this reason, we are using a wildcard mask with all 0s, and a 1 in the location where the bit changes:
0.0.0.2 in binary is 00000000.00000000.00000000.00000010
Unlike subnet masks, the 1s and 0s don’t need to be contiguous within the binary representation. They can appear in any combination.
The wildcard mask here says that the bit location set to 1 can be anything, but the bits set to 0 must remain the same. So, the ACL matches the following, where only the highlighted bit can be either 0 or 1.
11000000.10101000.00000001.00000101
The only two combinations that match such a situation are the following:
11000000.10101000.00000001.00000101
11000000.10101000.00000001.00000111
…which are 192.168.1.5 and 192.168.1.7.
It’s not intuitive, but it does work.
More complex non-contiguous example
Here’s a more complex example for which you might want to do the math. Let’s create an access list that will permit the following source IP addresses and deny all the rest:
- 192.168.1.5
- 192.168.1.9
- 192.168.1.13
- 192.168.1.17
The configuration that will achieve this is the following:
ip access-list extended NonContiguousACL2
permit ip 192.168.1.5 0.0.0.12 any
deny ip any any
To do the math, convert all the IP addresses to binary and determine which bits change between them and which remain the same. Create a wildcard mask with all 0s and set only those bits that change to 1, and you will get the wildcard mask of 0.0.0.12.
Conclusion
Wildcard masks offer a powerful and flexible way to define complex, non-contiguous IP address ranges in various network configurations, such as access control lists and routing protocols.
By understanding and leveraging their unique properties, network administrators can achieve granular control and optimization in their network management tasks.
Related Posts
- Comparison of BGP Confederations vs Route Reflectors
- What are BGP Confederations-Explanation and Discussion (With Cisco Example)
- What is BGP Route Reflector – Explanation and Discussion (with Cisco Example)
- Cisco Branch Virtual Office Solutions – Network Design
- Passing non-IP Traffic over IPSEC VPN using GRE over IPSEC