Imagine the following scenario: We have a web server on a DMZ protected by a Cisco ASA 5500 firewall. We would like to allow external Internet users to access this web server only after they successfully authenticate with a username/password credential.
Maybe this scenario could be applicable in situations where we need to allow employees to access a corporate intranet web server when they are away from the office.
The username/password accounts for the users could be stored either locally on the ASA firewall (not very scalable) or on an internal AAA (Authentication) Server, such as the Cisco Access Control Server (ACS). Let’s see an example diagram below to make things clear:
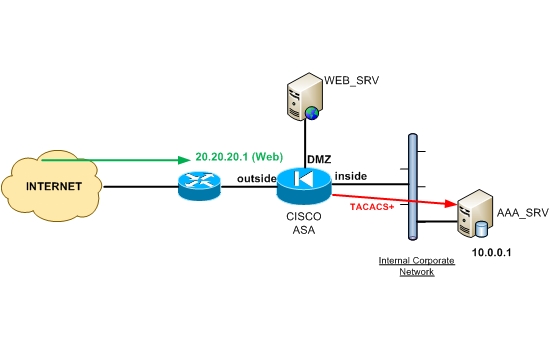
From the diagram above, assume that the Web Server (WEB_SRV) has a public IP address of 20.20.20.1.
Any access from outside to this IP address must be intercepted by the ASA firewall which should prompt the user for authentication (username/password).
After the user enters his/her credentials, the Firewall will communicate with the AAA Authentication server (AAA_SRV), using either TACACS+ or RADIUS protocols, to validate the credentials of the user.
The AAA server will respond to the firewall with ACCESS_PERMITED or ACCESS_DENIED accordingly.
If permitted, the user will be able to communicate with the Web Server. This functionality of the Cisco ASA Firewall is also called “cut-through Proxy” and works for only specific services (HTTP, HTTPs, FTP, and TELNET).
This means that in addition to authenticating users for Web Server access, we can do the same for FTP or TELNET Servers as well.
Configuration Example:
! Specify a AAA server name (AAA_SRV) and which protocol to use (Radius or TACACS+)
CISCO-ASA(config)# aaa-server AAA_SRV protocol tacacs+
! Designate the Authentication server IP address and the authentication secret key
CISCO-ASA(config)# aaa-server AAA_SRV (inside) host 10.0.0.1
CISCO-ASA(config-aaa-server-host)# key authentication-secret-key
! The following ACL specifies for which traffic flow the firewall will enforce authentication
CISCO-ASA(config)# access-list 120 permit tcp any host 20.20.20.1 eq www
! Enable web server user authentication by matching the ACL configured above
CISCO-ASA(config)# aaa authentication match 120 outside AAA_SRV
! The last statement above will authenticate traffic on the “outside” interface using
! server AAA_SRV only if this traffic matches Access List 120
Related Posts
- Introduction to Cisco EEM (Embedded Event Manager)
- Monitoring Cisco Network Infrastructure: What to Look for in an Ideal Cisco Monitoring Tool
- How to Reset Cisco Router or Switch to Factory Settings
- Comparison of LLDP vs CDP on Cisco Networking Devices
- Comparison of BGP Confederations vs Route Reflectors