The following article describes the proper way to allow BGP sessions between two routers to pass through a Cisco ASA firewall appliance.
Especially if the BGP configuration between the two routers uses MD5 authentication (which is a good security practice), you need some special “treatment” on this session in order to pass it successfully through an ASA device.
By default, the Cisco ASA does TCP Sequence Number Randomization to every session passing through it.
Also, the ASA will strip TCP option 19 by default. This TCP option (defined by RFC 2385) is a TCP extension to enhance security for BGP when using MD5 authentication.
The two actions above will cause problems to a BGP session when passing through the ASA and therefore we need to disable them.
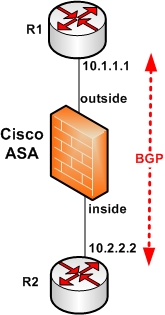
From the diagram above, first we need to match the BGP traffic between R1 and R2 using an Access Control List.
Then we must create a TCP Map that allows TCP Option 19 and also disable the TCP Sequence Number Randomization for this specific BGP traffic class.
Step1:
Match the BGP traffic with an ACL:
access-list bgp-traffic extended permit tcp host 10.1.1.1 host 10.2.2.2 eq bgp
access-list bgp-traffic extended permit tcp host 10.2.2.2 host 10.1.1.1 eq bgp
Step2:
Allow TCP option 19 with a TCP Map.
tcp-map ALLOW-TCP-19
tcp-options range 19 19 allow
Step3:
Create a class map to match the BGP Traffic using the ACL above.
class-map BGP-CLASS
match access-list bgp-traffic
Step4:
Use the Global Policy to apply all the actions:
policy-map global_policy
class BGP-CLASS
set connection random-sequence-number disable
set connection advanced-options ALLOW-TCP-19
What is TCP Option 19
This is a TCP extension used to carry an MD5 digest in a TCP segment, thus allowing BGP to work securely with MD5 and enhance its security.
The Cisco ASA firewall removes this TCP option from packets thus creates a problem in BGP sessions between two end-points that use MD5 authentication in BGP.
Related Posts
- Prevent Spoofing Attacks on Cisco ASA using RPF
- Configuring Connection Limits on Cisco ASA Firewalls – Protect from DoS
- Configuring AAA Authentication-Authorization-Accounting on Cisco ASA Firewall (TACACS+, RADIUS)
- Cisco ASA Firewall Management Interface Configuration (with Example)
- How to Configure Access Control Lists on a Cisco ASA 5500/5500-X Firewall (with Examples)