Although the Cisco ASA appliance does not act as a router in the network, it still has a routing table and it is essential to configure static or dynamic routing in order for the appliance to know where to send packets.
When a packet arrives to a network interface on the ASA firewall, the packet undergoes several security controls, such as ACL filtering, NAT, deep-packet inspection etc.
Routing Support on ASA
After the packet passes all firewall controls, the security appliance needs to send the packet to its destination address. It therefore checks its routing table to determine the outgoing interface where the packet will be sent.
Cisco ASA firewalls support both static and dynamic routing. For dynamic routing, the ASA supports RIPv2, EIGRP and OSPF.
I recommend not to use dynamic routing though and stick with just static routes. The reason is that one of the purposes of a firewall is to hide your internal trusted network addressing and topology. By configuring dynamic routing support, you might be advertising routes to untrusted networks thus exposing your network to threats.
Cisco ASA Static Route Configuration
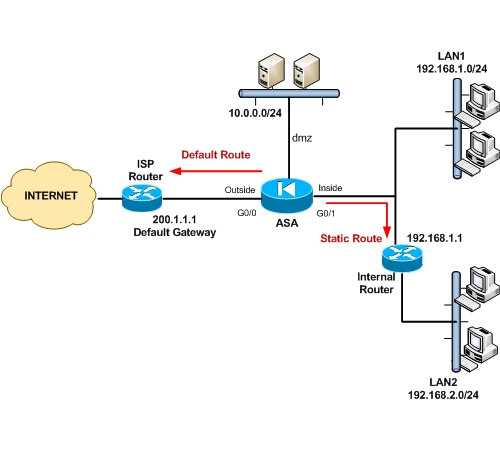
The scenario in the diagram above will help us understand how to configure static routing.
The ASA connects to the internet on the outside and also has a DMZ and Internal zones. The default gateway towards the ISP is 200.1.1.1. The DMZ network is 10.0.0.0/24 and the internal LAN1 network is 192.168.1.0/24.
LAN1 is directly connected to the Inside interface of the firewall. Additionally, there is another internal network, namely LAN2, with network 192.168.2.0/24. LAN2 is not directly connected to the firewall. Rather, there is an internal router with address 192.168.1.1 through which we can reach LAN2.
Therefore, in order for the ASA to reach network LAN2, we need to configure a static route to tell the firewall that network 192.168.2.0/24 can be reached via 192.168.1.1.
So we need to configure two static routes. One Default Static route for Internet access, and one internal static route to reach network LAN2. For directly connected networks (DMZ and LAN1) we don’t need to configure a static route since the firewall already knows about these networks as they are directly connected to its interfaces.
Static Route Configuration:
The format of the static route command is:
ASA(config)# route [interface name] [destination address] [netmask] [gateway]
! First configure a default static route towards the default gateway
ASA(config)# route outside 0.0.0.0 0.0.0.0 200.1.1.1
! Then configure an internal static route to reach network LAN2
ASA(config)# route inside 192.168.2.0 255.255.255.0 192.168.1.1
Verification Commands
Let’s now see how to check the routing table in the ASA appliance and verify the static route:
ASA#show route
Codes: C – connected, S – static, I – IGRP, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2, E – EGP
i – IS-IS, L1 – IS-IS level-1, L2 – IS-IS level-2, ia – IS-IS inter area
* – candidate default, U – per-user static route, o – ODR
P – periodic downloaded static route
Gateway of last resort is 200.1.1.1 to network 0.0.0.0
C 192.168.1.0 255.255.255.0 is directly connected, inside
S 192.168.2.0 255.255.255.0 [1/0] via 192.168.1.1, inside
C 200.1.1.0 255.255.255.0 is directly connected, outside
S* 0.0.0.0/0 [1/0] via 200.1.1.1
The routes denoted with “S” are the static routes and the ones denoted with “C” are the directly connected routes.
DOWNLOAD THIS ARTICLE AS PDF FILE
Related Posts
- Prevent Spoofing Attacks on Cisco ASA using RPF
- Configuring Connection Limits on Cisco ASA Firewalls – Protect from DoS
- Configuring AAA Authentication-Authorization-Accounting on Cisco ASA Firewall (TACACS+, RADIUS)
- Cisco ASA Firewall Management Interface Configuration (with Example)
- How to Configure Access Control Lists on a Cisco ASA 5500/5500-X Firewall (with Examples)