In this Video Tutorial I will show you how to enable initial access to the ASA device in order to connect with ASDM graphical interface or with SSH.
An out-of-the-box Cisco ASA device is not fully ready to be managed by the GUI interface (Adaptive Security Device Manager – ASDM). There is an initial configuration required to enable ASDM access to the firewall.
I know the above task in pretty basic but I hope it will help a few people that are just starting out with ASA firewalls.
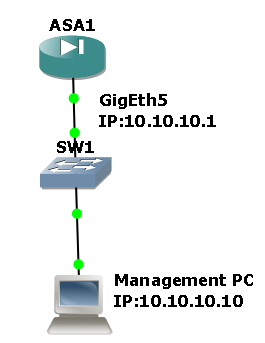
The network topology is shown below:
First we need to have console access (with a serial console cable) to the device in order to configure some initial settings to allow user access with ASDM or with SSH.
We will configure Interface GigabitEthernet 5 as a management interface with IP address 10.10.10.1/24.
Also, on the same subnet we have our management PC with IP address 10.10.10.10/24. The management PC is running also a TFTP server software (tftp32) which will be used to transfer the ASDM image to the ASA.
Below is the CLI configuration used in this initial setup (see video below also for more information):
ciscoasa# sh run
: Saved
:
ASA Version 8.4(2)
!
hostname ciscoasa
! Configure an “enable password” which is the administrator password of the device
enable password 2KFQnbNIdI.2KYOU encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface GigabitEthernet0
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
! Configure IP address to Interface GigEth5 and put a high security level (90 is good).
! name also the interface as “management”
interface GigabitEthernet5
nameif management
security-level 90
ip address 10.10.10.1 255.255.255.0
!
ftp mode passive
pager lines 24
mtu management 1500
icmp unreachable rate-limit 1 burst-size 1
! Tell the appliance where the asdm image is located.
asdm image disk0:/asdm-647.bin
no asdm history enable
arp timeout 14400
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
! SSH access will use the LOCAL username/password for authentication
aaa authentication ssh console LOCAL
! enable the HTTP service on the device so that you can connect to it for ASDM access
http server enable
! Tell the device which IP addresses are allowed to connect for HTTP (ASDM) access and from which interface
http 10.10.10.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
! Tell the device which IP addresses are allowed to connect for SSH access and from which interface.
ssh 10.10.10.0 255.255.255.0 management
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
! Configure a LOCAL username/password to be used for authentication.
username cisco password 3USUcOPFUiMCO4Jk encrypted
!
!
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email [email protected]
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
crashinfo save disable
Cryptochecksum:0760c72b39dd8d7a479d517a65758f33
: end
ciscoasa#
NOTE:
To enable SSH access, we need to generate also SSH keys as following:
ciscoasa(config)# crypto key generate rsa modulus 1024
Keypair generation process begin. Please wait…
ciscoasa(config)#
I have created the following video on youtube and thought about embedding the video here as well. It is about configuring the Cisco ASA in order to install the ASDM image (Adaptive Security Device Manager) and hence be able to manage the device with the graphical ASDM GUI.
The video shows also how to enable SSH access to the device, how to restrict access to a management network etc.
An out-of-the-box Cisco ASA device is not fully ready to be managed by the GUI interface (ASDM). There is an initial configuration required to enable ASDM access to the firewall.
I know the above task in pretty basic but I hope it will help a few people that are just starting out with ASA firewalls.
Related Posts
- Prevent Spoofing Attacks on Cisco ASA using RPF
- Configuring Connection Limits on Cisco ASA Firewalls – Protect from DoS
- Configuring AAA Authentication-Authorization-Accounting on Cisco ASA Firewall (TACACS+, RADIUS)
- Cisco ASA Firewall Management Interface Configuration (with Example)
- How to Configure Access Control Lists on a Cisco ASA 5500/5500-X Firewall (with Examples)