Whenever Microsoft releases security patches even for unsupported Operating Systems (such as Windows XP, Vista etc) then you must act immediately (as a company or administrator) because it’s always a serious issue.

This is what happened in May 14 when Microsoft released security patches for a critical software vulnerability affecting the Remote Desktop Protocol (RDP).
The patches were issued also for unsupported operating systems such as Windows XP and Vista which shows how critical this vulnerability is.
The specific operating systems which are affected by BlueKeep vulnerability (CVE-2019-0708) include Windows Vista, XP, 7, Windows Server 2003 and 2008.
In a nutshell, the security weakness (code named “BlueKeep”) is categorized as Remote Code Execution vulnerability and can cause full system compromise remotely even without authentication to the system.
Moreover, Microsoft warned that this specific weakness has the potential to be “wormable”. This means that attackers can create exploits and malware which can self-spread and propagate from system to system thus causing havoc to multiple unpatched servers or workstations.
The most prevalent and dangerous type of attack that can take advantage of such vulnerability is a ransomware outbreak similar to WannaCry attack in 2017. The later, took also advantage of a similarly critical Microsoft vulnerability (named “EternalBlue” which I described here) on SMBv1 service.
Back then, millions of systems in networks (including also critical health systems etc) were affected by WannaCry outbreak.
Now, BlueKeep has the potential to create similar disaster so you must patch your systems immediately.
How to Prevent and Fix BlueKeep
- First and foremost action is to patch all of your Windows machines (user workstations, servers etc) with the patches released by Microsoft. Even non-supported versions (XP, Vista, 2003) have patches available here.
- Block RDP port 3389 if not needed (using a network firewall or even the Windows firewall). Especially if port 3389 is accessible from the Internet, this is a huge mistake and you must either block it immediately or patch the system. Currently there are around 1 million unpatched windows machines on the Internet with exposed RDP port.
- Enable Network Level Authentication (NLA) for RDP connections. NLA requires authentication therefore a possible worm will not be able to propagate to machines having NLA.
- Similar to point 2 above, disabling Remote Desktop service (if it’s not required) will help to mitigate the issue.
How to Scan your network to find Vulnerable Hosts with BlueKeep
There is currently a scanner module available in Metasploit which is effective to scan and identify vulnerable hosts in networks.
You can also specify big IP address ranges and the scan is pretty fast from what I have found in my own testing.
I’m using Kali Linux in my work environment so I’ll be discussing how I scanned using Kali.
Step 1:
Update your Kali box so you can get latest modules for Metasploit.
apt-get update
apt-get upgrade
Step 2:
Start Metasploit console.
msfconsole
Step 3:
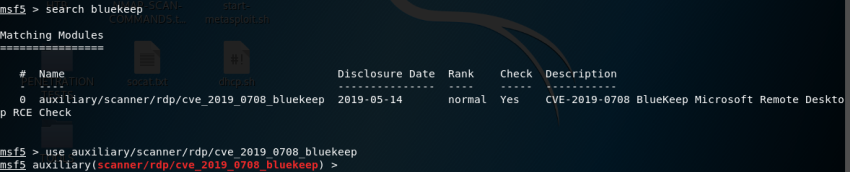
Search in msfconsole to find the Bluekeep scanner module as shown below:
search bluekeep
use auxiliary/scanner/rdp/cve_2019_0708_bluekeep
Step 4:
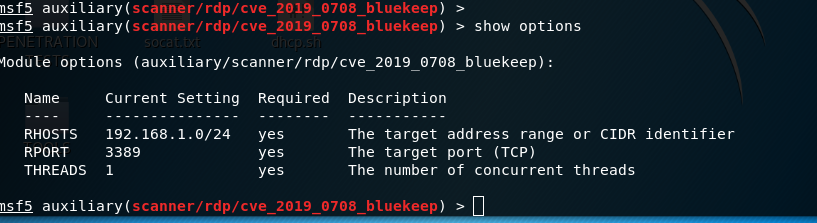
Set the target range to be scanned. In our example below, the range is 192.168.1.0/24
set RHOSTS 192.168.1.0/24
show options
Step 5:
Start the scanner using the “run” command in msfconsole. You can increase the THREADS to 5 for example for faster scanning if you want.
Here is a sample output from the scanner:
[*] 192.168.1.199:3389 – The target service is not running, or refused our connection.
[*] 192.168.1.200:3389 – The target service is not running, or refused our connection.
[+] 192.168.1.201:3389 – The target is vulnerable.
[*] 192.168.1.202:3389 – The target service is not running, or refused our connection
As you can see from above, the host with IP 192.168.1.201 is found to be vulnerable to BlueKeep.
Please let me know in the comments below if you have any questions.
Related Posts
- 5 Best Practices to Keep Rogue Devices at Bay
- Cisco Talos Year in Review – Top Cyber Security Threats in 2023 and Beyond
- How to Scan an IP Network Range with NMAP (and Zenmap)
- What is Cisco Identity Services Engine (ISE)? Use Cases, How it is Used etc
- What is Cisco Umbrella Security Service? Discussion – Use Cases – Features