Have you ever been in a situation where you needed to capture traffic going through a router? Have you ever wished you had a switch available to create a SPAN port? Have you ever asked why you took that small hub out of your computer bag? With all of these tools you could have simply hooked up and started capturing packet for analysis. Well, nevermore!
As of 12.3(4)T Cisco has introduced a feature that allow the administrator to configure a router to capture network traffic and review it for analysis. Have no fear “IP Traffic Exporter” is here!
Lets take a closer look at the configuration of IP Traffic Exporter.
*Note IP Traffic Exporter is applied before Packet Switching and Packet Filtering.
Configuration Tasks:
- Create ACL to match desired traffic.
- Create IP traffic exporter profile.
- Add the desired interface to the profile.
- Configure traffic direction with ACL.
- Apply traffic exporter to interface.
In the below image, we have created an ACL to match traffic sourced from 192.168.20.69.
![]()
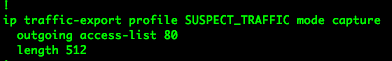
Next we have created the IP traffic exporter profile called SUSPECT_ TRAFFIC and set the mode to capture.
Inside the traffic-export config mode, we set the length of the packet to 512. We also tell the router that we want to capture outgoing traffic that matches ACL 80.
Just like many other items within IOS once you configure your settings, you must then apply them.
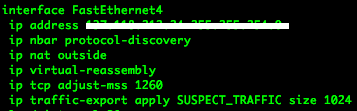
We enter interface configuration mode for the desired interface that we want to capture traffic on.
We apply the traffic-export by entering the following commands:
ip traffic-export apply SUSPECT_TRAFFIC size 1024
*Note: the size command sets the buffer size for the packets.
So still after all the configuration and applying the traffic-exporter… we must turn it on.
To do so, we enter the following commands from enable mode.
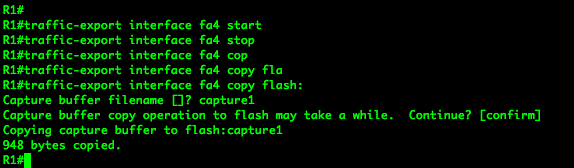
traffic-export interface fa4 start
This command starts the packet capture.
traffic-export interface fa4 stop
Well this command stops the capture.
traffic-export interface fa4 copy flash:
This command will copy the capture from the buffer to a file on flash. This capture can also be copied to a tftp or ftp server, and many other locations.
Verification:
To verify the capture completed correctly you can use your favorite packet analysis tool, my personal favorite is wireshark, to analyze the packets.
Related Posts
- Introduction to Cisco EEM (Embedded Event Manager)
- What is Cisco IOS – Overview and Description of Cisco’s Operating System
- How to Configure SNMP on Cisco Devices (Routers, Switches)
- Comparing Cisco IOS Configurations (Config Compare Tools)
- Cisco Access List Configuration Examples (Standard, Extended ACL) on Routers Etc