In this article we will consider the topic of Cisco IOS Zone Based Firewall (ZBFW). Cisco IOS Zone Based Firewall allows us to define Security Zones and to give each zone its own policy.
What is Zone Based Firewall
At the very beginning of Cisco routers, the implementation of firewall functionality on IOS router devices was done using the so called IOS firewall or CBAC (Context-Based Access Control).
The evolution of the above concept is “Zone Based Firewall” which is the newer form of configuring firewall traffic control on routers.
You might ask: “But traffic control can be achieved also using Access Control Lists (ACL)”
Yes, that’s correct but ACLs are NOT stateful. The Zone Based Firewall feature provides stateful inspection of traffic just like a regular hardware firewall.
You will need to create and configure security zones as explained below.
Security Zones Explained
Security Zone – interface or group of interfaces, on which a particular policy is applied. By default in the same Security Zone all traffic is permitted, but between security zones all traffic is blocked, except the traffic generated by the router. For permitting traffic between security zones, creating zone-pairs and policies for each zone are required.
Zone-pair – allows us to determine uni-directional firewall policy between zones. To put it simply, a zone-pair determines the direction of interesting traffic. The direction is determined between source and destination zones.
Zone policy – determines what kind of traffic should be denied or permitted between zones. For example: we want to permit HTTP traffic and deny SMTP traffic. Zone policy has three actions: “pass”, “drop” and “inspect”. Pass and drop actions have immediate effect on traffic, but Inspect action tells the router to use pre-defined class map for traffic filtration.
Configuration of Zone Based Firewall on Cisco Router
Let’s consider an example in details. In the following scenario, we will create two zones, inside and outside, and allow only PING (ICMP) for Inside Zone to pass to Outside Zone (not vice-versa).
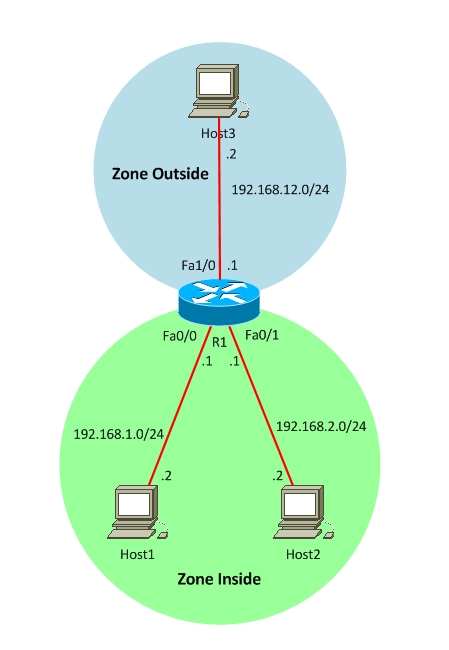
Before starting configuration of Zone Based Firewall, make sure that everything works and all hosts are connected to each other. We will need to identify interfaces that will belong in the same security zone and group them together.
! Create Inside and Outside Zones.
R1(config)#zone security INSIDE
R1(config)#zone security OUTSIDE
! Assign interfaces to Zones
R1(config)#interface fa0/0
R1(config-if)#zone-member security INSIDE
R1(config)#interface fa0/1
R1(config-if)#zone-member security INSIDE
R1(config)#interface fa1/0
R1(config-if)#zone-member security OUTSIDE
! Determine the interesting traffic by class-map.
R1(config)#class-map type inspect match-any CLASS_INSIDE_2_OUTSIDE
R1(config-cmap)#match protocol icmp
In class-map configuration parameters basically we use two parameters: match-any and match-all. In case of “match-any”, traffic can be matched to any match criteria, but in case of match-all the traffic must match all criteria, which are determined in Class-map. In our case we check only ICMP but we can match against any protocol that we need.
We’ve already determined what traffic we want to control and now we determine what to do with this traffic.
! Create policy map, which will check traffic.
R1(config)#policy-map type inspect POLICY_INSIDE_2_OUTSIDE
R1(config-pmap)#class type inspect CLASS_INSIDE_2_OUTSIDE
R1(config-pmap-c)#inspect
note: at the end of the policy map there is an implicit “deny all” by default, which looks like this :
class class-default
drop
At the end we need to determine the direction of Firewall control, which will be done by zone-pairs.
!Determine Zone-pairs and directions.
Router(config)#zone-pair security PAIR_INSIDE_2_OUTSIDE source INSIDE destination OUTSIDE
!Attach already created Policy-map to the zone pair.
Router(config-sec-zone-pair)#service-policy type inspect POLICY_INSIDE_2_OUTSIDE
Let’s do some checking. According to our scenario, hosts in Inside zone must ping hosts located in outside zone, but hosts in outside zone will not be able to ping hosts located in inside zone. Let’s see the result.
host1#ping 192.168.12.1
!!!!
host3#ping 192.168.1.2
…..
host3#ping 192.168.2.2
…..
That’s working as planned.
Related Posts
- Introduction to Cisco EEM (Embedded Event Manager)
- What is Cisco IOS – Overview and Description of Cisco’s Operating System
- How to Configure SNMP on Cisco Devices (Routers, Switches)
- Comparing Cisco IOS Configurations (Config Compare Tools)
- Cisco Access List Configuration Examples (Standard, Extended ACL) on Routers Etc