Generic Routing Encapsulation (GRE) and Internet Protocol Security (IPsec) are two related but distinctly different technologies.
They can be deployed separately but can also work together (GRE over IPSec) to deliver network tunneling and security services to networks and individual users.
In this article, we’ll explore these technologies to understand them, and compare them to identify the most common use cases of each.
Generic Routing Encapsulation (GRE)
GRE is a network tunneling protocol that is used for creating virtual private networks (VPNs). It establishes communication links between two remote networks or devices over an intermediary network such as the Internet.
It accomplishes this by encapsulating various network layer protocols within point-to-point connections. This encapsulation, referred to as tunneling, allows data packets to traverse networks that may or may not natively support the original protocol.
GRE Operation
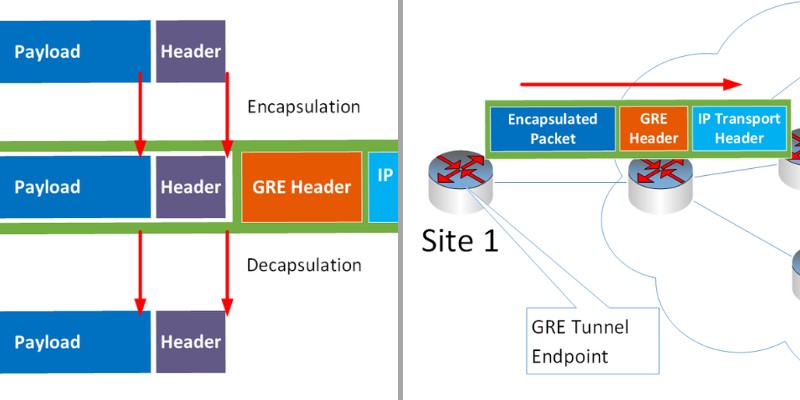
The following diagram shows an example of a GRE tunnel endpoint at Site 1 which encapsulates data packets by prepending a GRE header and an additional IP Transport header.
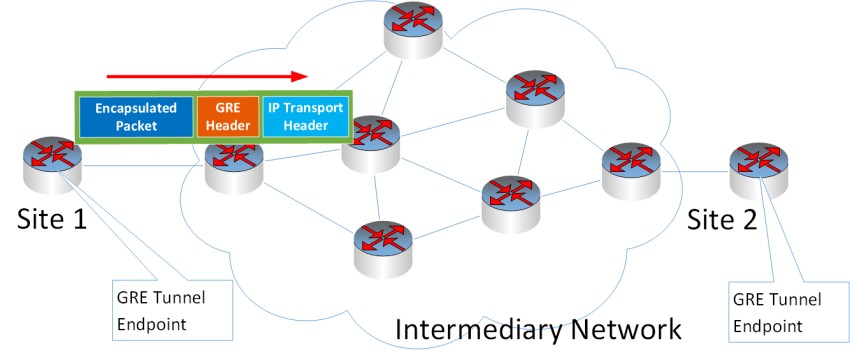
The encapsulated packet is tunneled, and the prepended transport IP header has the destination address of the intended GRE tunnel endpoint at Site 2.
Once the tunneled packet reaches the tunnel endpoint at Site 2, the transport IP header and the GRE header are removed, and the encapsulated packet is then routed based on its own header.
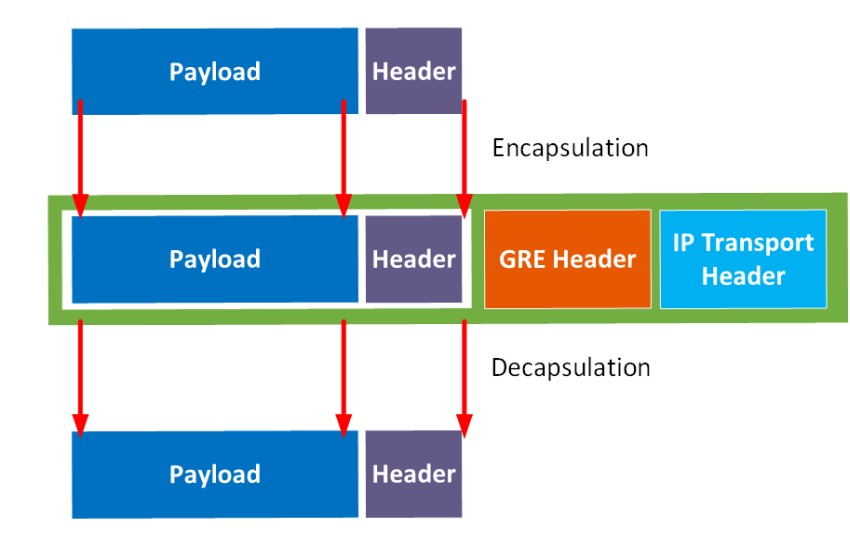
The following diagram gives us a close-up of the encapsulation and decapsulation process. Here you can see in more detail the header of the encapsulated packet.
GRE Security
It’s essential to note that GRE, by itself, does not provide encryption or authentication. Thus, it does not ensure the confidentiality of the transmitted data.
Instead, it focuses only on creating a tunnel for data transmission between remote sites. Therefore, GRE tunnels are often employed as a foundation, and other security protocols, such as IPsec, are employed to add layers of security like encryption and authentication to the communication.
Use Cases
GRE can be used to interconnect remote sites by creating VPNs. However, for the most part, GRE alone is rarely used due to its lack of security features.
GRE is more often used as the underlying technology of more modern VPN implementations such as Dynamic Multipoint VPNs (DMVPNs). GRE tunnels may also be employed between remote sites where dynamic routing protocols need to be supported since GRE supports multicast.
IPsec Protocol
IPsec is a comprehensive suite of protocols and technologies designed to enhance the security of Internet communications by encrypting and authenticating IP packets.
Operating at the Network Layer (Layer 3) of the OSI model, IPsec ensures the confidentiality, integrity, and authenticity of data transmitted over the network.
It is much more detailed and involved than GRE, and encompasses a whole series of algorithms, mechanisms, and implementations.
IPsec focus of Implementation
IPsec offers several critical features, including encryption, data integrity verification, data origin authentication, and protection against replay attacks.
These features collectively ensure that data remains confidential and immune to tampering or eavesdropping while it travels across networks.
It is not typically used to tunnel traffic, like GRE, but can be applied to tunnels like GRE to add encryption, authentication, and integrity to traffic traversing such tunnels.
Modes of Implementation
IPsec can be configured in two primary modes: Transport Mode and Tunnel Mode. In Transport Mode, only the payload of the IP packet is encrypted and authenticated, allowing for secure host-to-host communication.
In Tunnel Mode, the entire IP packet, including the original IP header, is encapsulated within a new IP packet. This mode is often used to secure network-to-network or site-to-site communications.
Use Cases
Common applications of IPsec include securing VPN connections of various types (GRE, MPLS, DMVPN, and others), enabling remote access or site-to-site VPN connections in corporate networks, and safeguarding sensitive data transmitted over the Internet.
It is an add-on capability for IPv4 and has been designed to be an integral part of IPv6 delivering inherent security features.
While IPsec is indeed capable of tunneling traffic, it’s essential to recognize that this functionality is not its primary focus.
The protocol’s main emphasis throughout its development has centered on ensuring the security, confidentiality, and authentication of data rather than being optimized for tunneling purposes.
Comparison Table of GRE vs IPSEC
The following table compares various aspects of the GRE protocol and the IPsec suite.
| Aspect | IPsec | GRE |
| Purpose | Security and authentication of data | Tunneling and encapsulation of data |
| Layer of Operation | Network Layer (Layer 3) | Network Layer (Layer 3) |
| Encryption | Yes, provides encryption for data | No encryption (can be added with other protocols) |
| Authentication | Yes, provides data origin authentication | No authentication (can be added with other protocols) |
| Data Integrity | Yes, ensures data integrity | No data integrity (can be added with other protocols) |
| Data Confidentiality | Yes, ensures data confidentiality | No data confidentiality (can be added with other protocols) |
| Routing Support | Limited routing support, often used with dynamic routing protocols | Can transport routing protocol traffic |
| Multicast Support | No, not natively, although it can be configured to do so | Natively supports multicast traffic |
| Tunnel Creation | Can create secure tunnels for data transport | Primarily used for creating tunnels |
| Encapsulation | Encrypts and encapsulates the entire original IP packet | Encapsulates the entire original IP packet without encryption |
| Protocols Supported | Compatible with various network layer protocols | Primarily used for IP packet encapsulation |
| Tunneling Purpose | Used for secure communication between networks or devices over untrusted networks (VPN) | Used for connecting different networks, routing, and encapsulating various protocols |
| Key Management | Utilizes key management protocols like IKE (Internet Key Exchange) | Key management typically handled separately (e.g., with IPsec for security) |
| Protocol Support | Often used in conjunction with other tunneling protocols (e.g., GRE) for enhanced security | Can be used as a standalone tunneling protocol or in combination with other protocols for added functionality |
| Authentication Methods | Supports various authentication methods, including pre-shared keys and digital certificates | No inherent authentication (depends on other protocols for this) |
It’s important to note that IPsec and GRE serve different primary purposes, with IPsec focusing on data security and authentication, while GRE primarily facilitates tunneling and encapsulation.
The comparison table may be considered by some as comparing apples to oranges, but the truth is that there is enough overlap and interoperation between these two technologies to make such a comparison meaningful and informative.
In practice, GRE and IPsec are often used together, with GRE providing the tunneling function and IPsec adding encryption and authentication for enhanced security when needed.
Conclusion
GRE serves as a tunneling protocol that facilitates the creation of communication links, called VPNs, over intermediary networks, providing remote sites and devices the ability to connect to a network as if they were in the same physical location.
IPsec is a suite of security protocols that add layers of encryption and authentication to IP packets of all types.
When used together, GRE and IPsec create a secure and private communication channel between networks or devices, ensuring the protection of data as it traverses potentially untrusted networks.