Layer 3 addressing can become difficult to manage in a network especially if you have an extensively large number of host devices.
With tens, hundreds, or even thousands of hosts in many enterprise networks, the need for an automated mechanism for assigning IP addresses and other network parameters was realized very early on.
In this article, we will examine and compare BOOTP vs DHCP, two distinct yet related protocols that can perform this automatic Layer 3 address assignment…and much more.
BOOTP
Bootstrap Protocol, most often written as BOOTP, is a protocol that was developed in the 1980s whose primary purpose was to enable a host device to be automatically assigned an IP address as well as to receive its boot image from a local network server.
It was developed at a time when host devices were considered “dumb terminals” without any local hard drive, and in some cases without local floppy disk drives.
When these terminals “boot up” they need to be able to pull themselves up from their own bootstraps so to speak (which is where the protocol gets its name from) and get to a state where they automatically obtain an IP address, find their boot image, and load up their operating system. BOOTP was developed for this very purpose.
BOOTP process
When a BOOTP host is started, it broadcasts a BOOTP request. This request contains the MAC address of the device itself, identifying the host making the request.
This request reaches all hosts on the local broadcast domain including the local BOOTP server on the network segment. The server replies to the client with a BOOTP response that contains the following information:
- The client’s IP address, subnet mask, and default gateway
- The IP address and host name of the BOOTP server
- The IP address of the server that contains the boot image
The host configures itself with these network parameters, contacts the server, and requests its boot image which contains the terminal’s operating system, downloads it, and loads it into memory.
The host proceeds to boot up from that image, completes the process, and is ready for use. Initially, BOOTP was limited to these basic capabilities, but as it developed, additional capabilities were added.
BOOTP usage today
BOOTP was used extensively for Unix-like diskless workstations as well as for quick rollouts of preconfigured clients using early versions of Windows for easy installation on newly installed hosts.
Today, BOOTP has been largely superseded and is rarely used. You may find it in some older devices, on some antiquated network printers, or some legacy diskless hosts.
It was originally defined in RFC 951, a standard that has been obsoleted several times. Indeed, RFC 2132 published in March 1997 was the last RFC where BOOTP was mentioned as a distinct protocol independent of its successor, namely, DHCP.
DHCP
Dynamic Host Configuration Protocol (DHCP) was originally introduced as an extension of BOOTP. Thus, DHCP has its roots in BOOTP, and may be considered a more advanced version or a newer incarnation of the original protocol.
Its initial purpose was to extend BOOTP’s capabilities to allow features including address leasing, as well as a wide variety of additional configuration options.
DHCP first appeared in RFC 1541 in 1993 as part of BOOTP. However, RFC 2131 published in 1997 was the first time that DHCP was described as a distinct protocol from BOOTP.
By the mid-2000s, all new networking equipment fully supported DHCP. DHCP’s roots in BOOTP can be seen today by the fact that it is backward compatible with BOOTP, and DHCP servers can successfully respond to BOOTP requests.
DHCP process
Based on BOOTP, DHCP’s process begins in a similar manner. All DHCP operations fall into four stages. These are:
- Discovery
- Offer
- Request
- Acknowledgement
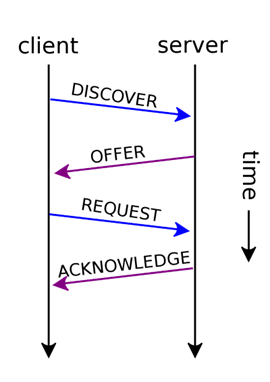
The following diagram describes this communication over time between the DHCP client and server.
By Gelmo96 – Own work, CC BY-SA 4.0, https://commons.wikimedia.org/w/index.php?curid=38179484
The client begins by broadcasting a DHCPDISCOVER message onto the local subnet. This message at the very least contains the client’s MAC address but it can also include a request to be assigned its last known IP address.
It may also request additional parameters such as a DNS server and a default gateway. In any case, a local DHCP server receives this message and processes it.
The DHCP server will respond by reserving an IP address for the client and makes what is known as a lease offer sent within a DHCPOFFER message, again as a broadcast.
This message contains the client’s MAC address, the offered IP address, subnet mask, lease duration, and the IP address of the DHCP server itself. It may also include additional parameters that were requested by the client.
Once the client receives this DHCPOFFER, it responds with a DHCPREQUEST requesting the offered address and parameters. A client may receive multiple responses from multiple DHCP servers, so the DHCPREQUEST contains the IP address of the DHCP server that it has accepted the lease from.
The DHCP server receives this DHCPREQUEST and responds with an DHCPACK. Once received by the client, the received parameters are configured, and the DHCP process is complete.
Comparing BOOTP vs DHCP
Since DHCP is essentially an advanced incarnation of BOOTP, these two protocols don’t really directly “compete” within a production network.
However it is useful to know and understand the differences between them and how the evolution of one protocol has led to the existence of the other.
The following table describes some of the details of these protocols, how they are similar, and how they differ:
| Characteristic | BOOTP | DHCP |
| First developed | 1985 | 1993 as an extension of BOOTP, 1997 as a distinct protocol |
| Originally published RFCs | RFC 951 | RFC 1541 |
| Primary purpose | Assign an IP address, find the boot image on the network, and load the operating system | Automatically assign IP addressing to hosts, as well as a multitude of additional network parameters and options |
| Compatibility | BOOTP is not forward compatible with DHCP | DHCP is backward compatible with BOOTP |
| Support for relay agent | Yes | Yes |
| Supports temporary IP addressing with lease times | No | Yes |
| Configuration | Manually configured MAC to IP correspondence on server | Automatic MAC to IP correspondence |
| Transport layer protocol | UDP | UDP |
| Server port | 67 | 67 |
| Client port | 68 | 68 |
| Support for options | Supports 19 options as defined in RFC 1497 vendor extensions | Supports up to 255 DHCP standardized as well as configurable options |
Conclusion
Network addressing protocols are a very useful tool when creating, designing, maintaining, and administrating networks.
BOOTP was born out of a need to enable hosts to automatically receive their network parameters as well as their boot image to operate.
As the needs of networks evolved, so too did BOOTP, into what we know as DHCP. Today, DHCP is an indispensable tool for managing large networks, and is extensively used in networks of all types, including enterprise networks, ISPs, wireless networks, as well as mobile communication networks.