In this article I will show you how to deny access to specific websites (domain names) with a normal Cisco ASA firewall.
This works on either the older 5500 models or the new 5500-X series devices. The only pre-requisite for the firewall is to run software version 8.4.2 and later. Also, you don’t need to have any next generation firewall features or special licenses installed.
Although the ASA can provide a simple solution for restricting web access to specific websites, you should know that it is NOT a replacement for a full-featured URL filtering solution.
There are a few methods to block access to websites. These methods include regular expressions (regex) together with Modular Policy Framework (MPF), finding the IP address of the website and blocking with ACL, and using FQDN in an ACL.
The first method (regex with MPF) works well with HTTP websites but it will not work at all if the website uses HTTPs.
The second method (blocking the IP with ACL) will work only for simple websites which have a static IP but it will be difficult to work for dynamic websites (such as Facebook, Twitter etc) which have many different IP addresses which change all the time.
The third method (using FQDN in an ACL) is the one which we will describe here.
From ASA version 8.4(2) and later, Access Control Lists (ACL) can contain an object which represents a Fully Qualified Domain Name (FQDN).
So, inside an ACL you can allow or deny access to hosts using their FQDN name instead of their IP address. You can therefore deny access to website www.facebook.com by denying access to FQDN object “www.facebook.com” inside the ACL.
The ASA will need to resolve all possible IP addresses of the FQDN and will dynamically insert several “deny IP” entries for these IP addresses in the ACL. Therefore you must specify what DNS server the ASA can use in order to resolve IP addresses for the FQDNs.
The method above does not slow down the firewall since the device will do the DNS lookup for the website you want to block beforehand and store all resolved IP addresses of the website in memory.
Depending on the TTL of the DNS lookup, the firewall will keep doing DNS requests for the specific domain name (every few hours for example) and update the resolved IPs in memory.
In our example network below, we want to restrict access to www.website.com which resolves to IP address 2.2.2.2. The ASA will use the internal DNS server (or any other DNS) to resolve the IP and put a “deny IP” entry in the inbound ACL applied on the “inside” interface.
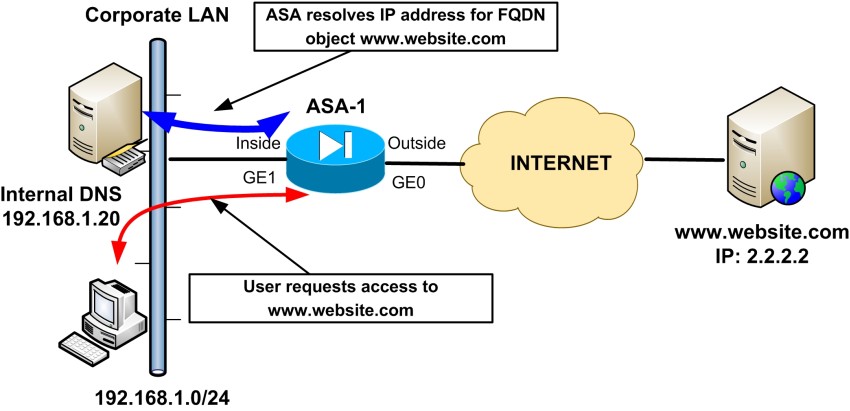
Let’s now see the required configuration on the ASA to achieve the above scenario:
domain-name mycompany.com
interface GigabitEthernet0
nameif outside
security-level 0
ip address 20.20.20.2 255.255.255.0
interface GigabitEthernet1
nameif inside
security-level 100
ip address 192.168.1.1
![other interface commands omitted]
!Specify which DNS server to use for resolving FQDN domains.
dns domain-lookup inside
dns server-group DefaultDNS
name-server 192.168.1.20
domain-name mycompany.com
!Create FQDN objects for website we want to block. Block both the www and non-www domains
object network obj-www.website.com
fqdn www.website.com
object network obj-website.com
fqdn website.com
!Add the FQDN objects above to an ACL applied inbound to the inside interface
access-list INSIDE-IN extended deny ip any object obj-www.website.com
access-list INSIDE-IN extended deny ip any object obj-website.com
access-list INSIDE-IN extended permit ip any any
!Apply the ACL above to the inside interface
access-group INSIDE-IN in interface inside
![other commands omitted]
Related Posts
- What is Cisco ASA Firewall – All you need to Know
- Traffic Rate and Bandwidth Limiting on Cisco ASA Firewall
- Cisco ASA Firewall (5500 and 5500-X) Security Levels Explained
- Cisco ASA 5505-5510-5520-5540-5550-5580 Performance Throughput and Specs
- Password Recovery for the Cisco ASA 5500 Firewall (5505,5510,5520 etc)