The CSC-SSM module of the Cisco ASA 5500 Firewall offers content security inspection for FTP, HTTP, POP3, and SMTP traffic, thus protecting the network from viruses, spyware, worms, spam and phishing, and controls unwanted mail and Web content. In more detail, the capabilities of the CSC-SSM module include the following:
- Antivirus and Antispyware protection using the Trend Micro technology.
- URL filtering
- content filtering
- email filtering
- anti-phishing protection in Web and email.
- Anti-spam protection in email.
After initial installation and configuration of the CSC-SSM module, you need to configure the ASA Firewall to send specific traffic to the module for inspection.
The traffic supported for inspection is FTP, HTTP, POP3 and SMTP as we mentioned above. For SMTP traffic, the inspection works only for inbound traffic from the Internet towards internal SMTP servers protected by the ASA appliance.
The flow of scanned traffic with the CSC-SSM module is shown on the figure below (figure courtesy of Cisco.com):
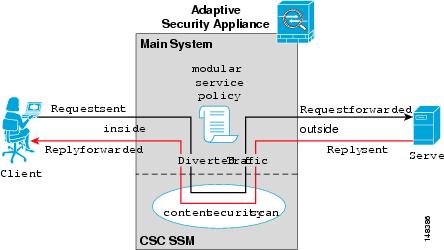
To configure the Cisco ASA Firewall to send traffic to the content inspection module we need to use the modular policy framework as following:
Configuring the Cisco ASA to work with CSC-SSM:
Assume we have an internal network range of 192.168.1.0/24. We want to configure the CSC-SSM module to inspect outbound HTTP, FTP, and POP3 traffic from our internal hosts towards the Internet.
! First define what traffic to inspect
ASA(config)# access-list inspect_outbound extended permit tcp 192.168.1.0 255.255.255.0 any eq 80
ASA(config)# access-list inspect_outbound extended permit tcp 192.168.1.0 255.255.255.0 any eq 21
ASA(config)# access-list inspect_outbound extended permit tcp 192.168.1.0 255.255.255.0 any eq 110
! Create a class map to identify the traffic that should be diverted to the CSC SSM
ASA(config)# class-map csc_outbound_class
ASA(config-cmap)# match access-list inspect_outbound
! Create a policy map and attach the class-map
ASA(config)# policy-map csc_out_policy
ASA(config-pmap)# class csc_outbound_class
ASA(config-pmap-c)# csc fail-open
! Apply the policy map globally or to a specific interface (inside in our case)
ASA(config-pmap-c)# service-policy csc_out_policy interface inside
The csc fail-open command under the policy-map controls how the adaptive security appliance handles traffic when the CSC SSM is unavailable. The fail-open keyword specifies that all traffic will be permitted in case the CSC module fails. The other option is fail-close.
Related Posts
- What is Cisco ASA Firewall – All you need to Know
- Traffic Rate and Bandwidth Limiting on Cisco ASA Firewall
- Cisco ASA Firewall (5500 and 5500-X) Security Levels Explained
- Cisco ASA 5505-5510-5520-5540-5550-5580 Performance Throughput and Specs
- Password Recovery for the Cisco ASA 5500 Firewall (5505,5510,5520 etc)