Prefix lists play an important role in networking by providing an efficient and scalable method for managing routing updates in large-scale networks.
As a tool for implementing route filtering, they enable network administrators to selectively control the advertisement and acceptance of IP prefixes based on specific criteria.
In this article, we’ll delve deeper into what prefix lists are and how they work, exploring their usage in various routing protocols and offering practical tips on their implementation in Cisco routers for optimized routing performance.
What is Route Filtering?
Route filtering, also known as prefix filtering, is a method of controlling the routing updates that are shared between routers by selectively advertising or accepting IP prefixes based on specific criteria.
Prefix filtering is an essential tool for network administrators to manage the distribution of routing information, optimize routing performance, and enhance network security.
Route filtering is typically applied on both incoming and outgoing routing protocol updates, and can be used with various routing protocols such as BGP, OSPF, and EIGRP. Various methods can be used to perform route filtering, including using access control lists (ACLs), route-maps, and prefix lists.
What are Prefix Lists?
Prefix lists are specially designed entities for filtering IP prefixes in routing updates. They are more efficient and scalable than ACLs, especially when dealing with extensively large numbers of IP prefixes.
Unlike ACLs, which are used in conjunction with a wide range of other features, the usage of prefix lists is confined to route filtering, redistribution, and route summarization.
Although they look similar to ACLs, they are quite different and are more powerful when filtering prefixes.
For example, let’s say we want to filter all prefixes within the 20.0.0.0 range that have subnet masks between /25 and /28.
Can you do it with ACLs? Yes, but with an unmanageably large number of statements. With a prefix list, it’s much easier to do.
Where ACLs define IP address ranges, prefix lists define lists of prefixes. If you’ve used ACLs a lot but haven’t really touched prefix lists, then it can be difficult to get your head around the concept. An example will help to understand how prefix lists work.
Prefix List Example 1
Let’s say we have the following scenario:
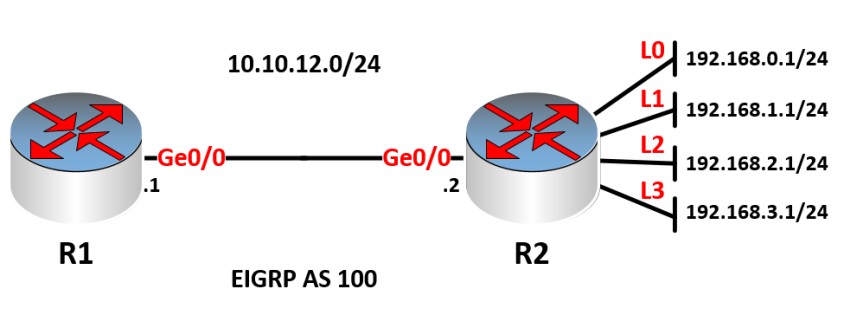
We have a topology where EIGRP is running on both routers, and all networks have been advertised. We have R2, which has four loopback interfaces with the addresses as shown.
EIGRP is advertising all four of those networks to R1. The result is that R1 has the following routing table:
R1#show ip route eigrp
192.168.0.0/24 is subnetted, 4 subnets
D 192.168.0.0 [90/156160] via 10.10.12.2, 00:01:07, GigabitEthernet0/0
D 192.168.1.0 [90/156160] via 10.10.12.2, 00:01:07, GigabitEthernet0/0
D 192.168.2.0 [90/156160] via 10.10.12.2, 00:01:07, GigabitEthernet0/0
D 192.168.3.0 [90/156160] via 10.10.12.2, 00:01:07, GigabitEthernet0/0
All of the networks connected to each loopback of R2 have been advertised to R1, and are found within its routing table.
Now let’s perform some filtering. Let’s start with a prefix list that filters 192.168.1.0/24 but permits everything else. We will create the prefix list on R1 and apply it to all incoming EIGRP updates:
R1(config)#ip prefix-list FILTER seq 5 deny 192.168.1.0/24
R1(config)#ip prefix-list FILTER seq 10 permit 0.0.0.0/0 le 32
Now the syntax appears somewhat similar to an access-list, but instead of using wildcards, it requires specifying the number of bits in the slash format.
The first line blocks the 192.168.1.0/24 network, while the second line allows 0.0.0.0/0, which is “all networks” with a subnet mask of /32 or smaller—essentially, this means “everything.” This line is equivalent to the “permit ip any any” statement of an ACL.
Now let’s apply this to the incoming EIGRP updates:
R1(config)#router eigrp 100
R1(config-router)#distribute-list prefix FILTER in
Let’s check out R1’s routing table again:
R1#show ip route eigrp
192.168.0.0/24 is subnetted, 4 subnets
D 192.168.0.0 [90/156160] via 10.10.12.2, 00:01:07, GigabitEthernet0/0
D 192.168.2.0 [90/156160] via 10.10.12.2, 00:01:07, GigabitEthernet0/0
D 192.168.3.0 [90/156160] via 10.10.12.2, 00:01:07, GigabitEthernet0/0
The 192.168.1.0/24 network has been filtered out.
Prefix List Example 2 – The power of ‘ge’ and ‘le’
Now at this point, you may say that this is not so difficult to do with an ACL, and you would be right. However, the real power of prefix lists is the use of the “greater than or equal to” and “less than or equal to” operators it uses. Using ge and le, you can specify whole ranges of prefix sizes. For example:
R1(config)#ip prefix-list TEST1 permit 10.0.0.0/8 le 19
This prefix list matches all prefixes that are within the range of 10.0.0.0/8 and have a subnet mask of /19 or smaller. So, this would match all of the following prefixes:
- 10.10.0.0/16
- 10.25.128.0/17
- 10.192.0.0/18
- 10.155.224.0/19
But all of the following prefixes would be denied, either because their subnet mask size is not less than 19 or because they are outside of the original IP address range:
- 10.10.255.0/24
- 192.168.0.0/16
- 10.96.8.0/21
- 172.16.0.0/19
Let’s put this into practice and use this TEST1 prefix list in our topology. First, let’s add some more loopback addresses to R2, advertise them using EIGRP, and remove our previous prefix list:
R2(config)#interface loopback 10
R2(config-if)#ip address 10.21.1.1 255.255.0.0
R2(config-if)#interface loopback 11
R2(config-if)#ip address 10.22.2.2 255.255.128.0
R2(config-if)#interface loopback 12
R2(config-if)#ip address 10.23.3.3 255.255.192.0
R2(config-if)#interface loopback 13
R2(config-if)#ip address 10.24.4.4 255.255.224.0
R2(config-if)#interface loopback 14
R2(config-if)#ip address 10.25.5.5 255.255.240.0
R2(config-if)#interface loopback 15
R2(config-if)#ip address 10.26.6.6 255.255.248.0
R2(config-if)#exit
R2(config)#router eigrp 100
R2(config-router)#network 10.0.0.0
R1(config-router)#no distribute-list prefix FILTER in
Notice the different subnet masks being used for each one of those networks. Next, let’s take a look at the routing table of R1 once again:
R1#show ip route eigrp
192.168.0.0/24 is subnetted, 4 subnets
D 192.168.0.0 [90/156160] via 10.10.12.2, 00:01:07, GigabitEthernet0/0
D 192.168.1.0 [90/156160] via 10.10.12.2, 00:01:07, GigabitEthernet0/0
D 192.168.2.0 [90/156160] via 10.10.12.2, 00:01:07, GigabitEthernet0/0
D 192.168.3.0 [90/156160] via 10.10.12.2, 00:01:07, GigabitEthernet0/0
10.0.0.0/8 is variably subnetted, 6 subnets, 6 masks
D 10.22.0.0/17 [90/156160] via 10.10.12.2, 00:02:22, GigabitEthernet0/0
D 10.23.0.0/18 [90/156160] via 10.10.12.2, 01:14:57, GigabitEthernet0/0
D 10.21.0.0/16 [90/156160] via 10.10.12.2, 00:06:11, GigabitEthernet0/0
D 10.26.0.0/21 [90/156160] via 10.10.12.2, 01:02:35, GigabitEthernet0/0
D 10.24.0.0/19 [90/156160] via 10.10.12.2, 01:14:46, GigabitEthernet0/0
D 10.25.0.0/20 [90/156160] via 10.10.12.2, 01:02:35, GigabitEthernet0/0
The new networks from R2 are advertised to R1 and are installed in the routing table. Now let’s apply the TEST1 prefix list we created before, to EIGRP updates coming into R1. Remember, it filters all prefixes in the range of 10.0.0.0/8 that have a prefix of 19 or less.
R1(config)#router eigrp 100
R1(config-router)#distribute-list prefix TEST1 in
Now lets took once again at the routing table of R1 to see what has been filtered out:
R1#show ip route eigrp
10.0.0.0/8 is variably subnetted, 6 subnets, 6 masks
D 10.22.0.0/17 [90/156160] via 10.10.12.2, 00:02:22, GigabitEthernet0/0
D 10.23.0.0/18 [90/156160] via 10.10.12.2, 01:14:57, GigabitEthernet0/0
D 10.21.0.0/16 [90/156160] via 10.10.12.2, 00:06:11, GigabitEthernet0/0
D 10.24.0.0/19 [90/156160] via 10.10.12.2, 01:14:46, GigabitEthernet0/0
Only four entries remain, and it is only those entries that adhere to our prefix list. All of the 192.168.X.X prefixes were removed because these are outside of the original range.
In addition, all of the prefixes within the original range that have a prefix value higher than 19 were also removed. So, what remains is the prefixes in the range of 10.0.0.0/8 with a prefix value of 19 or less.
Conclusion
While not as widely used as ACLs, prefix lists offer significantly greater capabilities for route filtering, particularly in larger networks with hundreds or thousands of networks where ACL-based filtering becomes cumbersome.
The ability to use prefix lists within the match clauses of route maps further enhances their versatility in practical applications. As with many aspects of networking, mastering prefix lists requires practice, which will help reveal their potential for optimizing larger network environments.