One of the easiest ways to configure simple remote access VPN functionality for your remote users is by configuring PPTP. This is supported on Cisco routers and will work with Windows OS flawlessly.

What is PPTP
PPTP (Point to Point Tunneling Protocol) is a quick and easy solution to offer remote access to users.
Since it is natively supported on almost all Windows operating systems (Windows XP, 7, 8, 10), this kind of remote access makes an ideal solution for clients using windows OS.
Also, you don’t need to install any additional software on the client machine.
However, you should note that PPTP does not offer the strong encryption and security offered by IPSEC or SSL VPN remote access solutions.
Although the Microsoft Point-to-Point Encryption (MPPE) supported by Cisco routers offers a good degree of security, PPTP remote access should not be used in situations where you need to provide access to high security resources and highly confidential data.
Like other types of remote access solutions, a remote user can use PPTP to connect to a corporate network and be treated as directly connected to that internal network even if he/she is physically outside the network.
PPTP is always implemented between a server (e.g a Cisco router) and a client (e.g a windows workstation). Cisco supports PPTP on its IOS routers. Cisco ASA firewalls do not support termination of PPTP on the firewall itself.
PPTP Client Configuration on Windows machines
There are numerous resources for configuring PPTP on windows machines. See some good tutorials below:
For Windows 7:
https://www.home-network-help.com/windows-7-pptp-vpn.html
For Windows 8:
https://my.ibvpn.com/knowledgebase/73/Set-up-the-PPTP-VPN-on-Windows-8.html
For Windows 10:
https://my.ibvpn.com/knowledgebase/267/Set-up-the-PPTP-on-Windows-10.html
Configuring PPTP on Cisco Router
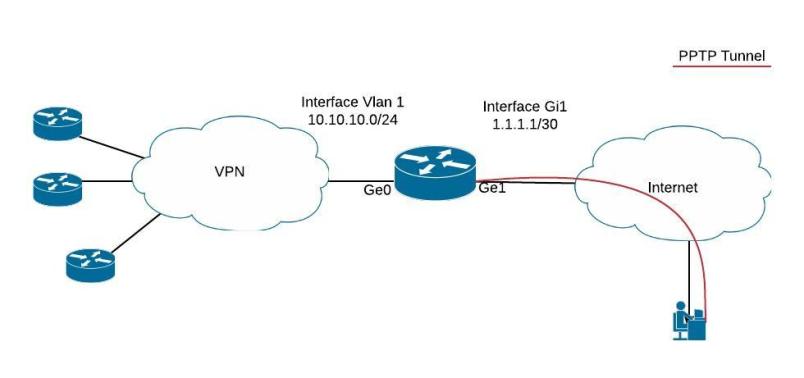
For this tutorial I propose the following scenario: The enterprise has a network with multiple sites connected via a VPN (this can be MPLS VPN, IPSEC VPN etc).
There is a single point connected to the internet and we need to offer a quick and easy remote access solution for teleworkers to access the whole network resources.
Assume that “Interface VLAN 1” with IP range 10.10.10.0/24 has routing access to the whole VPN network. If we “attach” the remote access users via the PPTP tunnel to this VLAN and assign them an IP address in the range 10.10.10.0/24, then they will have full access to the whole network resources.
In this scenario we will be authenticating users from local usernames configured on the Cisco router. For a more scalable and secure solution, I recommend using an external RADIUS server to authenticate users (or other AAA external server for full Authentication and Authorization control).
For this example our hardware is a cisco 867VAE-k9 with image c860vae-advsecurityk9-mz.152-4.M3.bin installed.
Configuration
The configuration needed to enable PPTP on the cisco router is described below :
vpdn enable <—- Enable VDPN (Virtual Private Dialup Network).
vpdn source-ip 1.1.1.1 < —– The IP used for the incoming connections
vpdn-group Networkstraining < ———— The name of the group
accept-dialin < —– Enables the router to accept dial in
protocol pptp < ———- Protocol to be used
virtual-template 1 < ———- The interface used for access
interface Virtual-Template1 < ——– The interface used for cloning
description PPTP Access
ip unnumbered Vlan1 < ———— Uses the IP configured on Vlan1 interface
ip virtual-reassembly in
load-interval 30
peer default ip address pool PPTP-Pool < —- Assign IP’s to clients in the range stated in PPTP-Pool
no keepalive
ppp encrypt mppe auto< —- Use Microsoft mppe encryption with automatically selected encryption strength (40, 56, or 128 bits)
ppp authentication ms-chap ms-chap-v2 < —- Configure the authentication methods allowed
ip local pool PPTP-Pool 10.10.10.90 10.10.10.100 < —— The range of IP’s that the dial in client will receive
username RemoteUser password letmein < ——– Creates a local username and password used for authentication. You can add more users here but we suggest a RADIUS server.
Other config :
interface GigabitEthernet1
description WAN Interface
ip address 1.1.1.1 255.255.255.252
interface Vlan1
description LAN Network
ip address 10.10.10.1 255.255.255.0
Verification commands:
show users
Line User Host(s) Idle Location
* 6 vty 0 admin idle 00:00:00
Interface User Mode Idle Peer Address
Vi3 RemoteUser PPPoVPDN 00:05:40 2.2.2.2
show vpdn
%No active L2F tunnels
%No active L2TP tunnels
PPTP Tunnel and Session Information Total tunnels 1 sessions 1
LocID Remote Name State Remote Address Port Sessions VPDN Group
182 estabd 2.2.2.2 37277 1 Networkstraining
LocID RemID TunID Intf Username State Last Chg Uniq ID
64 49152 182 Vi3 RemoteUser estabd 2d15h 63
DOWNLOAD ARTICLE AS PDF FILE
DOWNLOAD FULL CONFIGURATION FILE
Related Posts
- Introduction to Cisco EEM (Embedded Event Manager)
- What is Cisco IOS – Overview and Description of Cisco’s Operating System
- How to Configure SNMP on Cisco Devices (Routers, Switches)
- Comparing Cisco IOS Configurations (Config Compare Tools)
- Cisco Access List Configuration Examples (Standard, Extended ACL) on Routers Etc