A computer network is made up of software and hardware components that allow one device to communicate with another.
Hardware provides the set of instructions that utilizes the networking equipment for data transmission, whereas software specifies the sequence of commands (communication protocol) that uses the hardware equipment for data transmission.
A basic data transfer is made up of numerous phases that take place at different layers of the computer network. The most established communication stack is the OSI 7-layer model.
A communication network can also be categorized into two broad models:
- Peer-to-peer network model
- Client-Server network model
In this article we’ll go through Peer-to-Peer vs Client-Server based network models to learn how data is transmitted and received at the computer level and compare and discuss the two network communication categories.
Definition of Peer to Peer Model
A P2P (peer to peer) network is a decentralized collection of computers that has been established to exchange information (such as file documents, songs, movies, software, etc) with everyone or only certain users.
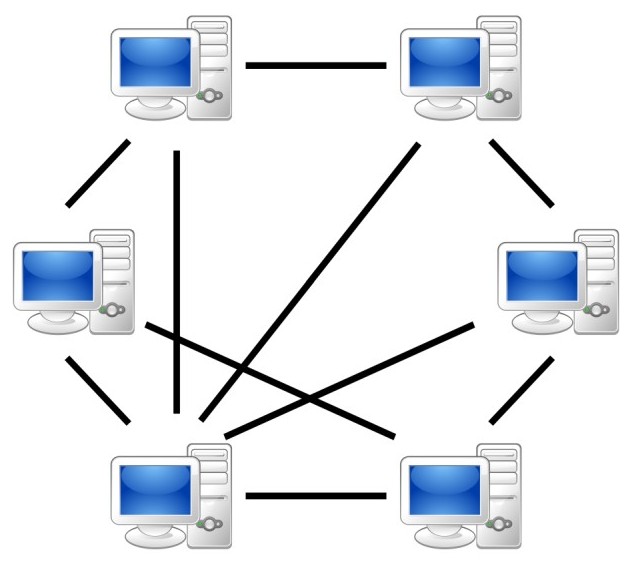
In a p2p network, all computers on the network are considered equal, with each workstation offering access to resources and data.
This means that each node in the p2p network model can both request for services from the other peers or offer services to the other peers. Each node can be both a client and a server.
Peer-to-Peer can be huge networks in which computers may interact with each other and share what is on or linked to their machines with other people.
It is also one of the most straightforward forms of architecture to construct if you have of course the proper software on each node.
Definition of Client-Server Model
The client-server model structure is a centralized network in which the server hosts, provides, and maintains the majority of the client’s data and services.
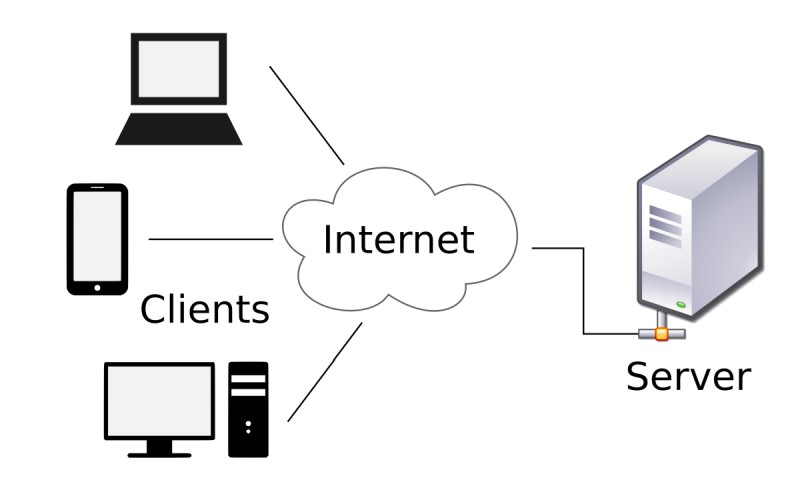
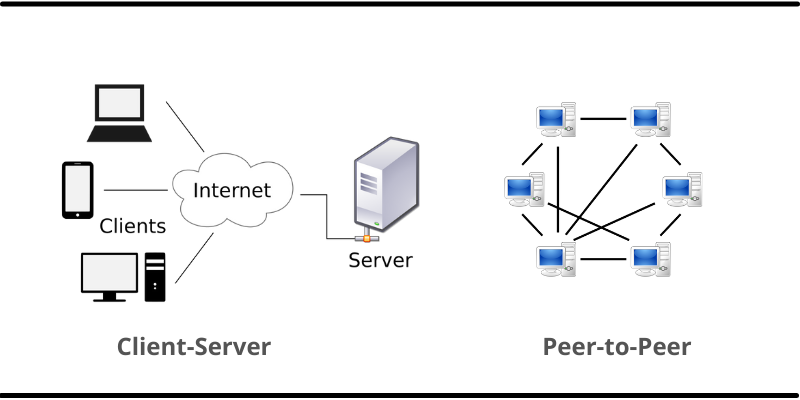
In this network model, a central server is a must and all the clients (computers) are connected to the central server for retrieving data or using its services.
The diagram above shows a server connected to the network (shown as Internet above but can be any other type of network) with various clients.
The server acts as a middle point of the network. Servers wait for requests from clients to show up before responding.
Comparison of Peer-to-Peer vs Client Server
| Characteristic | Client-Server Model | Peer-to-Peer Model (p2p) |
| Prime focus | Client-server networks are primarily concerned with data exchange. | peer-to-peer networks are primarily focused on communication and connectivity. |
| Data Transmission
|
In client-server networks, the server provides all the services and data while the clients request for services and data. | In a p2p network, all the members (peers) of the network act as the service providers and consumers.
|
| Cost | A client-server network is expensive to implement because a central server has to be built and it has to keep running constantly otherwise the network will collapse. | p2p is cheaper to make than a client-server network as no central server is required.
|
| Security | The client-server network model provides better security because the file access is controlled by the server, not the nodes.
|
A p2p network is more vulnerable. The peers act like the server and the consumer at the same time which is why file access can’t be handled centrally, the security is handled by the users. |
| Performance
|
Client-server systems are more robust and can be extended as needed.
|
As the number of nodes in a peer-to-peer network grows, performance decreases. |
| Bandwidth distribution
|
The bandwidth depends on the connection of the server to the rest of the network.
|
The full bandwidth is not allocated in advance in a peer-to-peer connection. It uses the bandwidth node according to the available bandwidth of each node (peer) and then releases it when it is no longer required. |
Examples of client-server architecture
Client-server networks are preferable for bigger networks, particularly if they are expected to increase in scale.
If your network contains sensitive data, you should employ a client-server structure as well.
When you use a web browser to go to a particular website, the browser (client) sends a request to the web server which is handling the website’s content.
Then the server responds to the request and sends data and cookies back to the browser which will show that data according to the configuration.
The same goes for database servers. The client sends a request/query to the server, which checks for the legitimacy of that request. If everything checks out, the server will send data back to the client.
Server peering is used in the Internet mail system, which is a distributed client-server framework.
Clients send and receive mail via communicating with servers, while servers communicate with one another.
An outgoing message can be sent directly to the server (MTA), which will transport it to the recipient’s inbox, or to another MTA, which will pass it on.
By organizing servers in a layer, this system is designed to be extremely scalable. Another example of distributed client-server is the DNS network which contains root servers and other second level servers in the hierarchy.
Examples of Peer to Peer (p2p) model
In 1999, when Napster was launched, was a pivotal moment in the history of P2P. People utilized Napster to exchange and download music via file-sharing programs.
Most of the music exchanged on Napster was copyrighted, making it unlawful to distribute it. That didn’t stop many from getting it, though.
Peer-to-peer technology had to face a lot of backlash because of its usage in illegal file-sharing (torrents). But a lot of companies and many day-to-day services we use, incorporate p2p technology.
Another example is Windows 10 updates. Microsoft’s servers and P2P are both used to deliver Windows 10 upgrades.
Some online gaming platforms make use of peer-to-peer (P2P) technology to allow players to download games. Diablo III, StarCraft II, and World of Warcraft are all distributed through peer-to-peer (P2P) by Blizzard Entertainment.
Because of blockchain’s peer-to-peer construction, all cryptocurrencies can be exchanged globally without the need of a middleman, mediators, or a central repository (server).
Anyone who wants to participate in the process of confirming and verifying blocks can set up a Bitcoin node on the decentralized peer-to-peer network.
In this process, the database is maintained by every member of the network, unlike banks where all the database is handled by a centralized server.
Pros & Cons of Peer to Peer Model
| Pros | Cons |
| Cheap because it does not need a central server. | It is generally slower because every user is accessed by other users.
|
| The network does not need a unique operating system to function.
|
Backing up data and archiving is tough because the files are handled by every user, not by a central server. |
| The speed of your internet connection may have no bearing on the time it takes for your files to download. | It is less secure than other network models.
|
| The system will not be disrupted if one of the computers crashes. | Possibilities of Illegal data sharing.
|
Pros & Cons of Client-Server Model
| Pros | Cons |
| Authorized users (clients) can access and modify data on a server, allowing for improved sharing.
|
When multiple client requests are made at the same time, servers become significantly saturated, resulting in traffic congestion. |
| Access and resources are better regulated on servers, ensuring that only authorized clients can acquire or alter data. | This network is vulnerable. If the server crashes, the whole network will collapse.
|
| Any new user can be simply integrated into the networks because the network is flexible enough. | Maintaining a central server can be costly and require a lot of manpower and time.
|
| Backing up and archiving data is easier in this network. | The user policies in the network must be set by an expert network administrator. |