An Access Control List (ACL) is a list of rules that control and filter traffic based on source and destination IP addresses or Port numbers. This happens by either allowing packets or blocking packets from an interface on a router, switch, firewall etc.

Individual entries or statements in an access lists are called access control entries (ACEs). Each ACE entry defines a traffic flow (source/destination) that will be either allowed or blocked.
In addition to traffic control and filtering in a network, ACLs can also be used as a security measure for connecting to your router by allowing only the necessary IP addresses or networks for accessing the router via telnet (or preferably with SSH).
They also have several other uses like management access control, route advertisement filtering, debug output filtering, traffic identification for encryption in VPN scenarios etc.
Access lists basically are a tool to match interesting packets which can then be subjected to different kinds of special operations.
On Cisco devices we have two main types of ACLs. These are Standard Access Control Lists and Extended Access Control Lists.
- Standard Access Lists
Standard access lists are the basic form of access list on Cisco routers that can be used to match packets by source IP address field in the packet header. These access lists are simpler to create and understand but packet matching options are also limited to only source address.
- Extended Access Lists
If you want to match packets on anything more than source IP address, you would need an extended access list: numbered or named. Extended access lists can filter on source and destination IP addresses, or a combination of addresses and several other fields such as TCP/UDP ports etc.
Both standard and extended access lists can be written in numbered or named format, which are just different ways to write access lists.
In terms of functionality, numbered and named access lists are equivalent. What you can achieve with a numbered access list can also be achieved with an equivalent named access list, and this applies to both standard and extended ACLs.
Some people favor the named format as it is probably more readable but both formats are widely used in practice and both are important for your Cisco certification exam.
Please refer to Table 1 to learn the range of numbers that can be used to create standard and extended numbered access lists.
Table 1 Access List Number Ranges
| Access List Type | Number Range |
| IP Standard Access Lists | 1-99 |
| IP Standard Access Lists (expanded range) | 1300-1999 |
| IP Extended Access Lists | 100-199 |
| IP Extended Access Lists (expanded range) | 2000-2699 |
We will be considering these access control lists, how they work and how to configure them on Cisco routers.
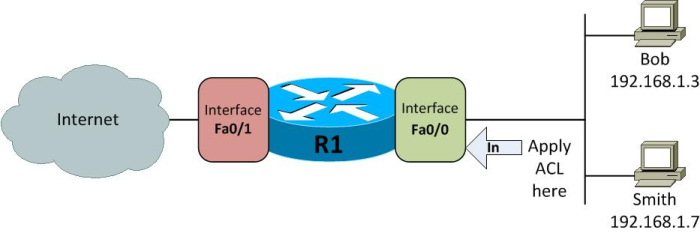
Please have a look at Figure 1 below that we will use for all our configuration examples.
The scenario consists of a single router R1 with two interfaces Fa0/0 and Fa0/1 connected to internal network and the Internet, respectively.
The access lists would be aimed at controlling access to the Internet by users in the internal network. These access lists would be applied to interface Fa0/0 in the inbound direction.
Figure 1 Access List Application
Standard Access List Configuration Examples
The standard access control list will allow you to either permit or deny traffic from a specific source IP address or IP network.
Creating Numbered Standard Access Lists
We will start by configuring a standard access list first in numbered and then in named format. The access list should allow Bob to access the Internet while block all access for Smith also logging unsuccessful attempts by Smith.
Let’s see how can we do this using a standard access list in numbered format.
R1>enable
R1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#access-list 1 permit host 192.168.1.3
R1(config)#access-list 1 deny host 192.168.1.7 log
R1(config)#
In the above configuration example we used host keyword to identify individual hosts but the same result can also be achieved by using inverse mask 0.0.0.0.
Let’s now apply this access list to interface Fa0/0 in the inbound direction.
R1(config)#interface Fa0/0
R1(config-if)#ip access-group 1 ?
in inbound packets
out outbound packets
R1(config-if)#ip access-group 1 in
R1(config-if)#end
R1#
Named access lists have a number from 1 to 99. When you are putting an access list on a router you will need to identify the access lists with a number e.g. access list 1 as shown above.
In every access list there will be an implicit deny all at the end of the ACL even if you don’t specify it explicitly. So if you configured your access list like this here is what it would do.
show access-list 1
The output will be:
access-list 1 permit host 192.168.1.3
access-list 1 deny host 192.168.1.7 log
access-list 1 deny any
Creating Named Standard Access Lists
Let’s now create an access list in the named format and apply it to interface Fa0/0, in order to achieve the same effect. Here, we would use the inverse mask instead of the host keyword to match individual hosts.
R1>enable
R1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#ip access-list standard Filter
R1(config-std-nacl)#permit 192.168.1.3 0.0.0.0
R1(config-std-nacl)#deny 192.168.1.7 0.0.0.0 log
R1(config-std-nacl)#interface Fa0/0
R1(config-if)#ip access-group Filter in
R1(config-if)#end
R1#
Extended Access Lists Configuration Examples
An extended access control list will allow you to deny or permit traffic from specific IP addresses, and ports.
It also gives you the ability to control the type of protocol that can be transferred such as ICMP, TCP, UDP and so forth. The range of the extended access control lists is from 100 to 199 for numbered ACLs.
An example of a numbered extended ACL:
access-list 110 permit tcp 92.128.2.0 0.0.0.255 any eq 80
The ACL 110 will permit traffic that is coming from any address on the 92.128.2.0 network (source network) towards any destination IP on port 80.
The ‘any’ statement is there so as to allow traffic towards any IP destination on port 80. The first network statement in the access-list command (i.e 92.128.2.0 0.0.0.255) refers to the source of the traffic, and the second network statement (the keyword “any” in our example) refers to the destination of the traffic.
Another example:
access-list 111 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
The above configuration will allow all IP traffic from source network 192.168.1.0/24 towards destination network 192.168.2.0/24.
Note also that the subnet mask in the ACL configuration in always represented with an inverse mask (i.e instead of using 255.255.255.0 we use 0.0.0.255).
Creating Numbered Extended Access Lists
We will now configure an extended access list first in numbered and then in named format. The access list should allow Bob (from our network diagram above) to access Web servers on the Internet while blocking all Web access for Smith also logging unsuccessful attempts by Smith to open a website.
Let’s see how we can do this using an extended access list in numbered format.
R1>enable
R1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#access-list 100 permit tcp host 192.168.1.3 any eq www
R1(config)#access-list 100 deny tcp host 192.168.1.7 any eq www log
R1(config)#interface Fa0/0
R1(config-if)#ip access-group 100 in
R1(config-if)#end
R1#
Creating Named Extended Access Lists
Now, let’s configure the same extended access list in the named format.
R1>enable
R1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#ip access-list extended Filter
R1(config-ext-nacl)#permit tcp 192.168.1.3 0.0.0.0 any eq www
R1(config-ext-nacl)#deny tcp 192.168.1.7 0.0.0.0 any eq www log
R1(config-ext-nacl)#interface Fa0/0
R1(config-if)#ip access-group Filter in
R1(config-if)#end
R1#
We briefly covered access lists in this article. You can verify which access lists exist on your Cisco device using command show access-lists.
A final access lists test is done by actually generating traffic that the access-list is supposed to permit or deny and see the results.
How to apply the ACL
After you have set the ACL in place you will need to specify which direction you want it to operate on the interface that will be applied (inbound or outbound).
For example “in” means inbound to the interface and “out” means outbound from the interface. The ACL is then applied on a specific interface using the “access-group” command.
You can identify an access list by giving it a name or number as discussed above. Here is a set of commands you would use:
Router(config)#interface serial 0
Router(config-if)#ip access-group 111 out
Using Access Lists to secure Telnet access to a router
You can also secure your telnet lines on a router via ACL. This will enable you to allow access to telnet login only for certain hosts or networks. Here is a sample configuration of how you would go about doing this.
access-list 25 permit 192.168.2.0 0.0.0.255
line vty 0 4
access-class 25 in
With this ACL in place you will only permit hosts on the 192.168.2.0/24 network to have access to the VTY login. All attempts from other networks would be blocked.
Another example: Let’s say we have one specific management station (10.1.1.1) which should be allowed to access the router via telnet. All other hosts should be blocked.
access-list 10 permit host 10.1.1.1
line vty 0 4
access-class 10 in